Share real and effective CompTIA Security+ SY0-501 exam dumps for free. 13 Online SY0-501 Exam Practice test questions and answers, online SY0-501 pdf download, easy to learn! Get the full SY0-501 Dumps: https://www.leads4pass.com/sy0-501.html (Total Questions: 543 Q&A) to make it easy to pass the exam!
The CompTIA Security+ exam will certify the successful candidate has the knowledge and skills required to install and configure systems to secure applications, networks, and devices; perform threat analysis and respond with appropriate mitigation techniques; participate in risk mitigation activities; and operate with an awareness of applicable policies, laws, and regulations. The successful candidate will perform these tasks to support the principles of confidentiality, integrity, and availability.
[PDF] Free CompTIA Security+ SY0-501 pdf dumps download from Google Drive: https://drive.google.com/open?id=1p48tIE7GSKFz_V895mWkWk7kaYHYEx0O
[PDF] Free Full CompTIA pdf dumps download from Google Drive: https://drive.google.com/open?id=1cFeWWpiWzsSWZqeuRVlu9NtAcFT4WsiG
CompTIA Security+ Certification - CompTIA IT Certifications: https://certification.comptia.org/certifications/security
Latest effective CompTIA Security+ SY0-501 Exam Practice Tests
QUESTION 1
A security analyst accesses corporate web pages and inputs random data in the forms. The response received includes
the type of database used and SQL commands that the database accepts. Which of the following should the security
analyst use to prevent this vulnerability?
A. Application fuzzing
B. Error handling
C. Input validation
D. Pointer dereference
Correct Answer: C
QUESTION 2
A database backup schedule consists of weekly full backups performed on Saturday at 12:00 a.m. and daily differential
backups also performed at 12:00 a.m. If the database is restored on Tuesday afternoon, which of the following is the
number of individual backups that would need to be applied to complete the database recovery?
A. 1
B. 2
C. 3
D. 4
Correct Answer: B
QUESTION 3
A web application is configured to target browsers and allow access to bank accounts to siphon money to a foreign
account.
This is an example of which of the following attacks?
A. SQL injection
B. Header manipulation
C. Cross-site scripting
D. Flash cookie exploitation
Correct Answer: C
QUESTION 4
During a third-party audit, it is determined that a member of the firewall team can request, approve, and implement a
new rule-set on the firewall.
Which of the following will the audit team most l likely recommend during the audit out brief?
A. Discretionary access control for the firewall team
B. Separation of duties policy for the firewall team
C. Least privilege for the firewall team
D. Mandatory access control for the firewall team
Correct Answer: B
QUESTION 5
A security administrator suspects that a DDoS attack is affecting the DNS server The administrator accesses a
workstation with the hostname of workstation01 on the network and obtains the following output from the if config
command: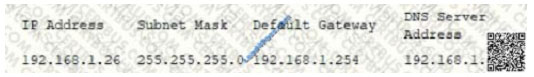 The administrator successfully pings the DNS server from the workstation. Which of the following commands should be
The administrator successfully pings the DNS server from the workstation. Which of the following commands should be
issued from the workstation to verify the DDoS attack is no longer occurring?
A. dig www.google.com
B. dig 192.168.1.254
C. dig workstationl.com
D. dig 192.168.1.26
Correct Answer: C
QUESTION 6
A penetration testing is preparing for a client engagement in which the tester must provide data that proves and
validates the scanning tools\\' results.
Which of the following is the best method for collecting this information?
A. Set up the scanning system\\'s firewall to permit and log all outbound connections
B. Use a protocol analyzer to log all pertinent network traffic
C. Configure network flow data logging on all scanning system
D. Enable debug level logging on the scanning system and all scanning tools used.
Correct Answer: A
QUESTION 7
An incident responder receives a call from a user who reports a computer is exhibiting symptoms consistent with a
malware infection. Which of the following steps should the responder perform NEXT?
A. Capture and document necessary information to assist in the response.
B. Request the user capture and provide a screenshot or recording of the symptoms.
C. Use a remote desktop client to collect and analyze the malware in real time.
D. Ask the user to back up files for later recovery.
Correct Answer: A
QUESTION 8
While reviewing the security controls in place for a web-based application, a security controls assessor notices that
there are no password strength requirements in place. Because of this vulnerability, passwords might be easily
discovered using a brute force attack.
Which of the following password requirements will MOST effectively improve the security posture of the application
against these attacks? (Select two)
A. Minimum complexity
B. Maximum age limit
C. Maximum length
D. Minimum length
E. Minimum age limit
F. Minimum re-use limit
Correct Answer: AD
QUESTION 9
A security administrator has been assigned to review the security posture of the standard corporate system image for
virtual machines. The security administrator conducts a thorough review of the system logs, installation procedures, and
network configuration of the VM image. Upon reviewing the access logs and user accounts, the security administrator
determines that several accounts will not be used in production.
Which of the following would correct the deficiencies?
A. Mandatory access controls
B. Disable remote login
C. Host hardening
D. Disabling services
Correct Answer: C
QUESTION 10
A security administrator suspects a MITM attack aimed at impersonating the default gateway is underway. Which of the
following tools should the administrator use to detect this attack? (Select two.)
A. Ping
B. Ipconfig
C. Tracert
D. Netstat
E. Dig
F. Nslookup
Correct Answer: BC
QUESTION 11
Which of the following is a document that contains detailed information about actions that include how something will be
done, when the actions will be performed, and penalties for failure?
A. MOU
B. ISA
C. BPA
D. SLA
Correct Answer: D
QUESTION 12
An organization has hired a penetration tester to test the security of its ten web servers. The penetration tester is able to
gain root/administrative access in several servers by exploiting vulnerabilities associated with the implementation of
SMTP, POP, DNS, FTP, Telnet, and IMAP.
Which of the following recommendations should the penetration tester provide to the organization to better protect their
web servers in the future?
A. Use a honeypot
B. Disable unnecessary services
C. Implement transport layer security
D. Increase application event logging
Correct Answer: B
QUESTION 13
To reduce disk consumption, an organization\\'s legal department has recently approved a new policy setting the data
retention period for sent email at six months. Which of the following is the BEST way to ensure this goal is met?
A. Create a daily encrypted backup of the relevant emails.
B. Configure the email server to delete the relevant emails.
C. Migrate the relevant emails into an "Archived" folder.
D. Implement automatic disk compression on email servers.
Correct Answer: A
CompTIA Security+ is the first security certification IT professionals should earn. It establishes the core knowledge required of any cybersecurity role and provides a springboard to intermediate-level cybersecurity jobs. Security+ incorporates best practices in hands-on trouble-shooting to ensure security professionals have practical security problem-solving skills. Cybersecurity professionals with Security+ know how to address security incidents – not just identify them.
Share 13 of the latest CompTIA Security+ SY0-501 exam questions and answers for free to help you improve your skills and experience! Easily select the complete SY0-501 Dumps: https://www.leads4pass.com/sy0-501.html (Total Questions: 543 Q&A) through the exam! Guaranteed to be
true and effective! Easily pass the exam!
[PDF] Free CompTIA Security+ SY0-501 pdf dumps download from Google Drive: https://drive.google.com/open?id=1p48tIE7GSKFz_V895mWkWk7kaYHYEx0O
[PDF] Free Full CompTIA pdf dumps download from Google Drive: https://drive.google.com/open?id=1cFeWWpiWzsSWZqeuRVlu9NtAcFT4WsiG
leads4pass Promo Code 12% Off

related: https://www.meetexams.com/latest-cisco-600-509-dumps-exam-practice/