Latest updates Cisco CCNP Security Implementing Cisco Secure Mobility Solutions (SIMOS v1.0) 300-209 exam questions and Answers! Free sharing 300-209 pdf online download, online exam Practice test, easy to improve skills! Get the full 300-209 exam dumps: https://www.leads4pass.com/300-209.html (Total questions:393 Q&A). Year-round updates! guarantee the first attempt to pass the exam!
[PDF] Free Cisco 300-209 pdf dumps download from Google Drive: https://drive.google.com/open?id=1cqN80_ksLXlLmH-XmP-JP8ejIScAfH8G
[PDF] Free Full Cisco pdf dumps download from Google Drive: https://drive.google.com/open?id=1CMo2G21nPLf7ZmI-3_hBpr4GDKRQWrGx
300-209 SIMOS - Cisco: https://www.cisco.com/c/en/us/training-events/training-certifications/exams/current-list/specialist-simos.html
Latest effective Cisco 300-209 Exam Practice Tests
QUESTION 1
Which header is used when a data plane IPsec packet is created?
A. IKEv1
B. AES
C. SHA
D. ESP
Correct Answer: D
QUESTION 2
Which algorithm is replaced by elliptic curve cryptography in Cisco NGE?
A. 3DES
B. AES
C. DES
D. RSA
Correct Answer: D
QUESTION 3
Which two operational advantages does GetVPN offer over site-to-site IPsec tunnel in a private MPLS-based core
network? (Choose two.)
A. Key servers perform encryption and decryption of all the data in the network, which allows for tight security policies.
B. Traffic uses one VRF to encrypt data and a different on to decrypt data, which allows for multicast traffic isolation.
C. GETVPN is tunnel-less, which allows any group member to perform decryption and routing around network failures.
D. Packets carry original source and destination IP addresses, which allows for optimal routing of encrypted traffic.
E. Group Domain of Interpretation protocol allows for homomorphic encryption, which allows group members to operate
on messages without decrypting them
Correct Answer: CD
http://www.cisco.com/c/en/us/products/collateral/security/group-encrypted-transport-
vpn/deployment_guide_c07_554713.html
QUESTION 4
An engineer must set up DMPN Phase2 with EIGRP to ensure spoke-to-spoke communication. Which two EIGRP
features must be disabled?
A. stub routing
B. split horizon
C. route redistribution
D. auto-summary
E. next-hop self
Correct Answer: BE
QUESTION 5
Which command clears all Cisco AnyConnect VPN sessions on a Cisco ASA?
A. vpn-sessiondb logoff anyconnect
B. vpn-sessiondb logoff webvpn
C. clear crypto isakmp sa
D. vpn-sessiondb logoff l2l
Correct Answer: A
QUESTION 6
Which two option, are benefits of AES compared to 3DES? (Choose two.)
A. switches encryption keys every 32 GB of data transfer
B. faster encryption
C. shorter encryption keys
D. longer encryption block length
E. repeating encryption keys
Correct Answer: BD
QUESTION 7
The Cisco AnyConnect client is unable to download an updated user profile from the ASA headend using IKEv2. What
is the most likely cause of this problem?
A. User profile updates are not allowed with IKEv2.
B. IKEv2 is not enabled on the group policy.
C. A new profile must be created so that the adaptive security appliance can push it to the client on the next connection
attempt.
D. Client Services is not enabled on the adaptive security appliance.
Correct Answer: D
QUESTION 8
A company has acquired a competitor whose network infrastructure uses only IPv6. An engineer must configure VPN
access sourced from the new company. Which remote access VPN solution must be used?
A. GET VPN
B. Any Connect
C. EzVPN
D. DMVPN
Correct Answer: C
QUESTION 9
What does DART stand for?
A. Device and report tool
B. Diagnostic Anyconnect Reporting Tool
C. Delivery and Reporting Tool
D. Diagnostics and Reporting Tool
Correct Answer: D
QUESTION 10
Which option describes the purpose of the shared argument in the DMVPN interface command tunnel protection IPsec
profile ProfileName shared?
A. shares a single profile between multiple tunnel interfaces
B. allows multiple authentication types to be used on the tunnel interface
C. shares a single profile between a tunnel interface and a crypto map
D. shares a single profile between IKEv1 and IKEv2
Correct Answer: A
QUESTION 11
Using the Next Generation Encryption technologies, which is the minimum acceptable encryption level to protect
sensitive information?
A. AES 92 bits
B. AES 128 bits
C. AES 256 bits
D. AES 512 bits
Correct Answer: B
QUESTION 12
Refer to the exhibit. What is the problem with the IKEv2 site-to-site VPN tunnel?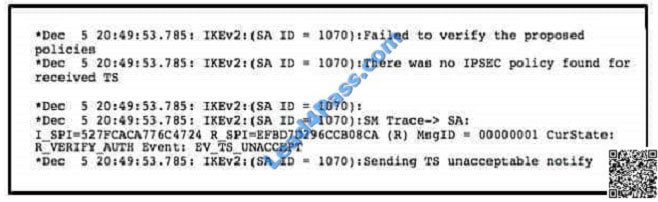 A. incorrect PSK
A. incorrect PSK
B. crypto access list mismatch
C. incorrect tunnel group
D. crypto policy mismatch
E. incorrect certificate
Correct Answer: B
QUESTION 13
You have been using pre-shared keys for IKE authentication on your VPN.
Your network has grown rapidly, and now you need to create VPNs with numerous IPsec peers.
How can you enable scaling to numerous IPsec peers?
A. Migrate to external CA-based digital certificate authentication.
B. Migrate to a load-balancing server.
C. Migrate to a shared license server.
D. Migrate from IPsec to SSL VPN client extended authentication.
Correct Answer: A
QUESTION 14
Which functionality is provided by L2TPv3 over FlexVPN?
A. the extension of a Layer 2 domain across the FlexVPN
B. the extension of a Layer 3 domain across the FlexVPN
C. secure communication between servers on the FlexVPN
D. a secure backdoor for remote access users through the FlexVPN
Correct Answer: A
QUESTION 15
A company has a Flex VPN solution for remote access and one of their Cisco any Connect remote clients is having
trouble connecting property. Which command verifies that packets are being encrypted and decrypted?
A. show crypto session active
B. show crypto ikev2 stats
C. show crypto ikev1 sa
D. show crypto ikev2 sa
E. show crypto session detail
Correct Answer: E
QUESTION 16
Which option is one of the difference between FlexVPN and DMVPN?
A. flexvpn uses ikev2 and dmvpn can use ikev1 or ikev2
B. dmvpn can use ikev1 and ikev2 where flexvpn only uses ikev1
C. flexvpn can use ikev1 and ikev2 where dmvpn uses only ikev2
D. dmvp uses ikev1 and flexvpn use ikev3
Correct Answer: A
QUESTION 17
An IOS SSL VPN is configured to forward TCP ports. A remote user cannot access the corporate FTP site with a Web
browser. What is a possible reason for the failure?
A. The user\\'s FTP application is not supported.
B. The user is connecting to an IOS VPN gateway configured in Thin Client Mode.
C. The user is connecting to an IOS VPN gateway configured in Tunnel Mode.
D. The user\\'s operating system is not supported.
Correct Answer: B
http://www.cisco.com/c/en/us/support/docs/security/ssl-vpn-client/70664-IOSthinclient.html
Thin-Client SSL VPN (Port Forwarding)
A remote client must download a small, Java-based applet for secure access of TCP applications that use static port
numbers. UDP is not supported. Examples include access to POP3, SMTP, IMAP, SSH, and Telnet. The user needs
local
administrative privileges because changes are made to files on the local machine. This method of SSL VPN does not
work with applications that use dynamic port assignments, for example, several FTP applications.
QUESTION 18
Which protocol must be enabled on the inside interface to use cluster encryption in SSL VPN load balancing?
A. TLS
B. DTLS
C. IKEv2
D. ISAKMP
Correct Answer: D
QUESTION 19
An engineer is configuring SSL VPN for remote access. A real-time application that is sensitive to packet delays will be
used. Which feature should the engineer confirm is enabled to avoid latency and bandwidth problems associated with
SSL connections?
A. DTLS
B. DPD
C. SVC
D. IKEv2
Correct Answer: A
QUESTION 20
A temporary worker must use clientless SSL VPN with an SSH plug-in, in order to access the console of an internal
corporate server, the projects.xyz.com server. For security reasons, the network security auditor insists that the
temporary
user is restricted to the one internal corporate server, 10.0.4.18.
You are the network engineer who is responsible for the network access of the temporary user.
What should you do to restrict SSH access to the one projects.xyz.com server?
A. Configure access-list temp_user_acl extended permit TCP any host 10.0.4.18 eq 22.
B. Configure access-list temp_user_acl standard permit host 10.0.4.18 eq 22.
C. Configure access-list temp_acl webtype permit url ssh://10.0.4.18.
D. Configure a plug-in SSH bookmark for host 10.0.4.18, and disable network browsing on the clientless SSL VPN
portal of the temporary worker.
Correct Answer: C
QUESTION 21
Refer to the exhibit. Which VPN solution does this configuration represent?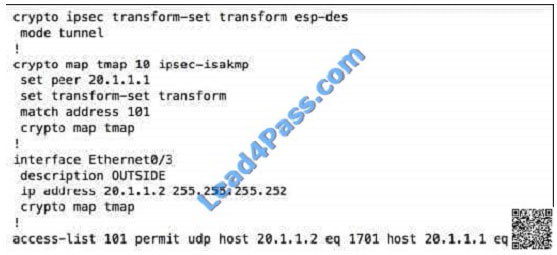
A. Cisco AnyConnect
B. IPsec
C. L2TP
D. SSL VPN
Correct Answer: B
QUESTION 22
Which two GDOI encryption keys are used within a GET VPN network? (Choose two.)
A. key encryption key
B. group encryption key
C. user encryption key
D. traffic encryption key
Correct Answer: AD
QUESTION 23
Which Cisco adaptive security appliance command can be used to view the count of all active VPN sessions?
A. show vpn-sessiondb summary
B. show crypto ikev1 sa
C. show vpn-sessiondb ratio encryption
D. show iskamp sa detail
E. show crypto protocol statistics all
Correct Answer: A
QUESTION 24
Refer to the exhibit. Given the partial configuration shown, which two statements are correct? (Choose two.)
crypto ipsec transform-set MY_TRANSFORM esp-aes 128 esp-sha-hmac! crypto ipsec profile MYPROFILE
set transform-set MY_TRANSFORM ! interface Tunnel0
ip unnumbered GigabitEthernet1/1
tunnel source GigabitEthernet1/1
tunnel destination 192.168.2.200
tunnel mode ipsec ipv4
tunnel protection ipsec profile MYPROFILE! ip route 10.1.2.0 255.255.255.0 Tunnel0
A. The tunnel will use the routing protocol configured for GigabitEthemet 1/1 for all tunnel communication with the peer.
B. The IP route statement to reach the remote network behind the DMVPN peer is incorrect, it should be ip route
192.168.2.0 255.255.255.0 tunnel 0.
C. This is an example of a static point-to-point VTI tunnel.
D. The tunnel will use esp-sha-hmac encryption in ESP tunnel mode.
E. The tunnel will use 128-bit AES encryption in ESP tunnel mode.
Correct Answer: CE
QUESTION 25
Which option describes the purpose of the command show derived-config interface virtual-access 1?
A. It verifies that the virtual access interface is cloned correctly with per-user attributes.
B. It verifies that the virtual template created the tunnel interface.
C. It verifies that the virtual access interface is of type Ethernet.
D. It verifies that the virtual access interface is used to create the tunnel interface.
Correct Answer: A
QUESTION 26
What URL do you use to download a packet capture file in a format which can be used by a packet analyzer?
A. ftp:///capture//
B. https:////
C. https:///admin/capture//pcap
D. https:////pcap
Correct Answer: C
QUESTION 27
Which two statements about the Cisco ASA Clientless SSL VPN solution are true? (Choose two.)
A. When a client connects to the Cisco ASA WebVPN portal and tries to access HTTP resources through the URL bar,
the client uses the local DNS to perform FQDN resolution.
B. The rewriter enable command under the global webvpn configuration enables the rewriter functionality because that
feature is disabled by default.
C. A Cisco ASA with an AnyConnect Premium Peers license can simultaneously allow Clientless SSL VPN sessions
and AnyConnect client sessions.
D. Content rewriter functionality in the Clientless SSL VPN portal is not supported on Apple mobile devices.
E. Clientless SSLVPN provides Layer 3 connectivity into the secured network.
Correct Answer: CD
QUESTION 28
Which feature is enabled by the use of NHRP in a DMVPN network?
A. host routing with Reverse Route Injection
B. BGP multiaccess
C. host to NBMA resolution
D. EIGRP redistribution
Correct Answer: C
QUESTION 29
Which Cisco IOS VPN feature simplifies IPsec VPN configuration and design by using on- demand virtual access
interfaces that are cloned from a virtual template configuration?
A. GET VPN
B. dynamic VTI
C. static VTI
D. GRE tunnels
E. GRE over IPsec tunnels
F. DMVPN
Correct Answer: B
QUESTION 30
Which command clears all crypto configuration from a Cisco Adaptive Security Appliance?
A. clear configure crypto
B. clear configure crypto ipsec
C. clear crypto map
D. clear crypto ikev2 sa
Correct Answer: A
QUESTION 31
Which VPN feature allows remote access clients to print documents to local network printers?
A. Reverse Route Injection
B. split tunneling
C. loopback addressing
D. dynamic virtual tunnels
Correct Answer: B
QUESTION 32
Which technology can rate-limit the number of tunnels on a DMVPN hub when system utilization is above a specified
percentage?
A. NHRP Event Publisher
B. interface state control
C. CAC
D. NHRP Authentication
E. ip nhrp connect
Correct Answer: C
QUESTION 33
When initiating a new SSL or TLS session, the client receives the server SSL certificate and validates it. After validating
the server certificate, what does the client use the certificate for?
A. The client and server use the server public key to encrypt the SSL session data.
B. The server creates a separate session key and sends it to the client. The client decrypts the session key by using the
server public key.
C. The client and server switch to a DH key exchange to establish a session key.
D. The client generates a random session key, encrypts it with the server public key, and then sends it to the server.
Correct Answer: D
QUESTION 34
Which three actions can be applied to a traffic class within a type inspect policy map? (Choose three.)
A. drop
B. priority
C. log
D. pass
E. inspect
F. reset
Correct Answer: ACF
QUESTION 35
Refer to the exhibit. A network administrator is running DMVPN with EIGRP, when the administrator looks at the routing
table on spoken 1 it displays a route to the hub only.
Which command is missing on the hub router, which includes spoke 2 and spoke 3 in the spoke 1 routing table?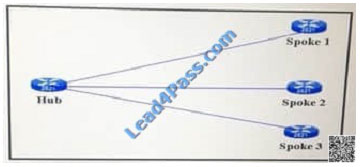
A. no inverse arp
B. neighbor (ip address)
C. no ip split-horizon egrp 1
D. redistribute static
Correct Answer: C
QUESTION 36
A company\\'s remote locations connect to data centers via MPLS.
A new request requires that unicast traffic that exist the remote location be encrypted.
Which no tunneled technology can be used to satisfy this requirement?
A. SSL
B. GET VPN
C. DMVPN
D. EzVPN
Correct Answer: B
QUESTION 37
Which type of communication in a FlexVPN implementation uses an NHRP shortcut?
A. spoke to hub
B. spoke to spoke
C. hub to spoke
D. hub to hub
Correct Answer: B
QUESTION 38
Which two troubleshooting steps should be taken when Cisco AnyConnect cannot establish an IKEv2 connection, while
SSL works fine? (Choose two.)
A. Verify that the primary protocol on the client machine is set to IPsec.
B. Verify that AnyConnect is enabled on the correct interface.
C. Verify that the IKEv2 protocol is enabled on the group policy.
D. Verify that ASDM and AnyConnect are not using the same port.
E. Verify that SSL and IKEv2 certificates are not referencing the same trustpoint.
Correct Answer: AC
QUESTION 39
Refer to the exhibit. The IKEv2 tunnel between Router1 and Router2 is failing during session establishment. Which
action will allow the session to establish correctly?
A. The address command on Router2 must be narrowed down to a /32 mask.
B. The local and remote keys on Router2 must be switched.
C. The pre-shared key must be altered to use only lowercase letters.
D. The local and remote keys on Router2 must be the same.
Correct Answer: B
QUESTION 40
Which three parameters are specified in the isakmp (IKEv1) policy? (Choose three.)
A. the hashing algorithm
B. the authentication method
C. the lifetime
D. the session key
E. the transform-set
F. the peer
Correct Answer: ABC
This is the latest update released by the Cisco CCNP Security Implementing Cisco Secure Mobility Solutions (SIMOS v1.0) 300-209 exam questions and answers, and we share 40 exam questions and answers for free to help you improve your skills! You can download 300-209 pdf or watch the 300-209 YouTube video tutorial online! Get the full 300-209 exam dumps: https://www.leads4pass.com/300-209.html (Total questions:393 Q&A). Help you pass the exam quickly!
[PDF] Free Cisco 300-209 pdf dumps download from Google Drive: https://drive.google.com/open?id=1cqN80_ksLXlLmH-XmP-JP8ejIScAfH8G
[PDF] Free Full Cisco pdf dumps download from Google Drive: https://drive.google.com/open?id=1CMo2G21nPLf7ZmI-3_hBpr4GDKRQWrGx
leads4pass Promo Code 12% Off

We share more practical and effective exam dumps
(Cisco,Microsoft,Oracle,Citrix,Comptia…) The latest citrix CCP-M 1y0-371 exam dumps help you improve your skills