
Easily get the latest Cisco CCNA Cyber Ops 210-255 dumps, “Implementing Cisco Cybersecurity Operations (SECOPS)” 210-255 Exam. You can upgrade your skills by downloading the 210-255 pdf or the online 210-255 exam exercise test! 99.5% pass rate:leads4pass.com
Table of Contents:
- Latest Nicky Cisco CCNA Cyber Ops 210-255 pdf
- Latest Cisco CCNA Cyber Ops 210-255 Practice Questions and Answers
- Latest Cisco CCNA Cyber Ops 210-255 YouTube videos:
- Related 210-255 Popular Exam resources
- leads4pass Promo Code 12% Off
- Why Choose leads4pass?
Latest Nicky Cisco CCNA Cyber Ops 210-255 pdf
[PDF] Free Cisco CCNA Cyber Ops 210-255 pdf dumps download from Google Drive: https://drive.google.com/open?id=1DvJqIWfL52ROsKHiVgNW44JumpzOCCj_
[PDF] Free Full Cisco pdf dumps download from Google Drive: https://drive.google.com/open?id=1CMo2G21nPLf7ZmI-3_hBpr4GDKRQWrGx
210-255 SECOPS – Cisco: https://www.cisco.com/c/en/us/training-events/training-certifications/exams/current-list/secops.html
Latest Cisco CCNA Cyber Ops 210-255 Practice Questions and Answers
QUESTION 1
Which statement about threat actors is true?
A. They are any company assets that are threatened.
B. They are any assets that are threatened.
C. They are perpetrators of attacks.
D. They are victims of attacks.
Correct Answer: C
QUESTION 2
Which process is being utilized when IPS events are removed to improve data integrity?
A. data normalization
B. data availability
C. data protection
D. data signature
Correct Answer: A
QUESTION 3
Which of the following are the three metrics, or andquot; scores,andquot; of the Common Vulnerability Scoring System
(CVSS)? (Select all that apply.)
A. Baseline score
B. Base score
C. Environmental score
D. Temporal score
Correct Answer: BCD
QUESTION 4
Which CVSSv3 metric value increases when the attacker is able to modify all files protected by the vulnerable
component?
A. confidentiality
B. integrity
C. availability
D. complexity
Correct Answer: B
QUESTION 5
Which two potions are the primary 5-tuple components? (Choose two)
A. destination IP address
B. header length
C. sequence number
D. checksum
E. source IP address
Correct Answer: AE
QUESTION 6
Refer to the Exhibit. A customer reports that they cannot access your organization\\’s website. Which option is a
possible reason that the customer cannot access the website?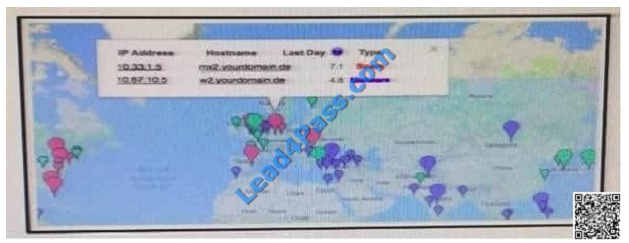
A. The server at 10.33.1.5 is using up too much bandwidth causing a denial-of-service.
B. The server at 10.67.10.5 has a virus.
C. A vulnerability scanner has shown that 10.67.10.5 has been compromised.
D. Web traffic sent from 10.67.10.5 has been identified as malicious by Internet censors.
Correct Answer: D
QUESTION 7
Which of the following are not components of the 5-tuple of flow in NetFlow? (Select all that apply.)
A. Source IP address
B. Flow record ID
C. Gateway
D. Source port
E. Destination port
Correct Answer: BC
QUESTION 8
Which CVSS metric describes the conditions that are beyond the attacker\\’s control that must exist to exploit the
vulnerability?
A. User interaction
B. Attack vector
C. attack complexity
D. privileges required
Correct Answer: C
QUESTION 9
Which signature type results in a legitime alert been dismissed?
A. True negative
B. False negative
C. True Positive
D. False Positive
Correct Answer: B
QUESTION 10
Which element is included in an incident response plan?
A. organization mission
B. junior analyst approval
C. day-to-day firefighting
D. siloed approach to communications
Correct Answer: A
QUESTION 11
Which of the following Linux file systems not only supports journaling but also modifies important data structures of the
file system, such as the ones destined to store the file data for better performance and reliability?
A. GRUB
B. LILO
C. Ext4
D. FAT32
Correct Answer: C
QUESTION 12
Refer to the exhibit. You notice that the email volume history has been abnormally high. Which potential result is true?
A. Email sent from your domain might be filtered by the recipient.
B. Messages sent to your domain may be queued up until traffic dies down.
C. Several hosts in your network may be compromised.
D. Packets may be dropped due to network congestion.
Correct Answer: C
QUESTION 13
Which of the following is one of the main goals of the CSIRT?
A. To configure the organization\\’s firewalls
B. To monitor the organization\\’s IPS devices
C. To minimize and control the damage associated with incidents, provide guidance for mitigation, and work to prevent
future incidents
D. To hire security professionals who will be part of the InfoSec team of the organization.
Correct Answer: C
All of our exam dumps are updated throughout the year, follow us! Get the latest recommendations! Pass the Cisco CCNA Cyber Ops 210-255 exam We recommend: https://www.leads4pass.com/210-255.html (176 Q&A).
Related 210-255 Popular Exam resources
| title | youtube | 210-255 SECOPS – Cisco | leads4pass | leads4pass Total Questions | |
|---|---|---|---|---|---|
| Cisco 210-255 | leads4pass 210-255 dumps pdf | leads4pass 210-255 youtube | 210-255 SECOPS – Cisco | https://www.leads4pass.com/210-255.html | 176 Q&A |
| Cisco CCNA Cyber Ops | https://www.leads4pass.com/210-250.html | 1100 Q&A |
leads4pass Promo Code 12% Off

Why Choose leads4pass?
leads4pass helps you pass the exam easily! We compare data from all websites in the network, other sites are expensive,
and the data is not up to date, leads4pass updates data throughout the year. The pass rate of the exam is above 98.9%.
