leads4pass Latest Update Microsoft AZ-500 Dumps Issues! The latest AZ-500 exam questions help you pass the exam successfully! All questions are updated to ensure true and effective! Welcome to Download leads4pass AZ-500 VCE Dumps or PDF Dumps: https://www.leads4pass.com/az-500.html (Total Questions: 203 Q&A AZ-500 Dumps)
Meetexams Exam Table of Contents:
- Latest Microsoft AZ-500 google drive
- Effective Microsoft AZ-500 Practice testing questions
- leads4pass Year-round Discount Code
- What are the advantages of leads4pass?
Latest Microsoft AZ-500 google drive
[PDF] Free Microsoft AZ-500 pdf dumps download from Google Drive: https://drive.google.com/file/d/1zbpomewbVYQK6t2wFwxYtIyde1qhArS6/
Latest updates Microsoft AZ-500 exam practice questions
QUESTION 1
You have an Azure subscription that contains 100 virtual machines. Azure Diagnostics is enabled on all the virtual
machines.
You are planning the monitoring of Azure services in the subscription.
You need to retrieve the following details:
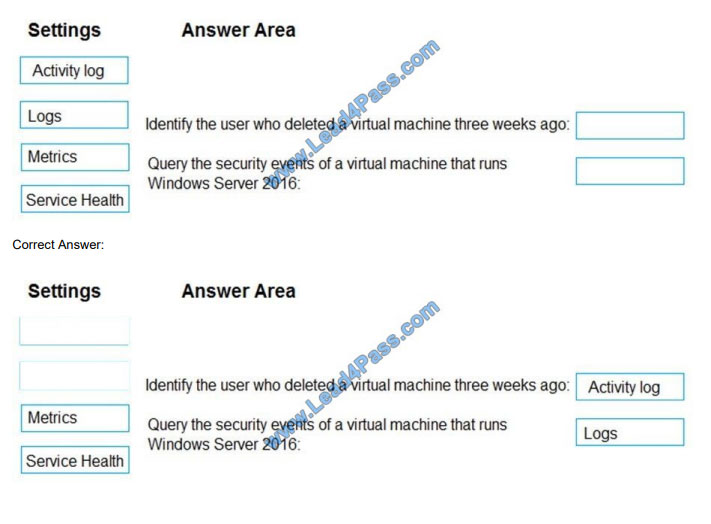
Identify the user who deleted a virtual machine three weeks ago.
Query the security events of a virtual machine that runs Windows Server 2016.
What should you use in Azure Monitor? To answer, drag the appropriate configuration settings to the correct details.
Each configuration setting may be used once, more than once, or not at all. You may need to drag the split bar between
panes or scroll to view content.
NOTE: Each correct selection is worth one point.
Select and Place:
QUESTION 2
You have an Azure subscription that contains the virtual machines shown in the following table.
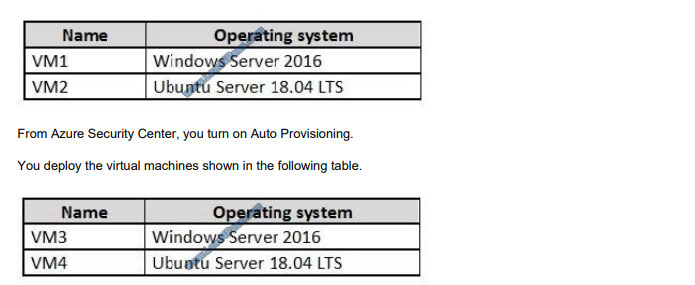
On which virtual machines is the Log Analytics agent installed?
A. VM3 only
B. VM1 and VM3 only
C. VM3 and VM4 only
D. VM1, VM2, VM3, and VM4
Correct Answer: D
When automatic provisioning is On, Security Center provisions the Log Analytics Agent on all supported Azure VMs and
any new ones that are created.
Supported Operating systems include: Ubuntu 14.04 LTS (x86/x64), 16.04 LTS (x86/x64), and 18.04 LTS (x64) and
Windows Server 2008 R2, 2012, 2012 R2, 2016, version 1709 and 1803
Reference:
https://docs.microsoft.com/en-us/azure/security-center/security-center-enable-data-collection
QUESTION 3
You have an Azure key vault.
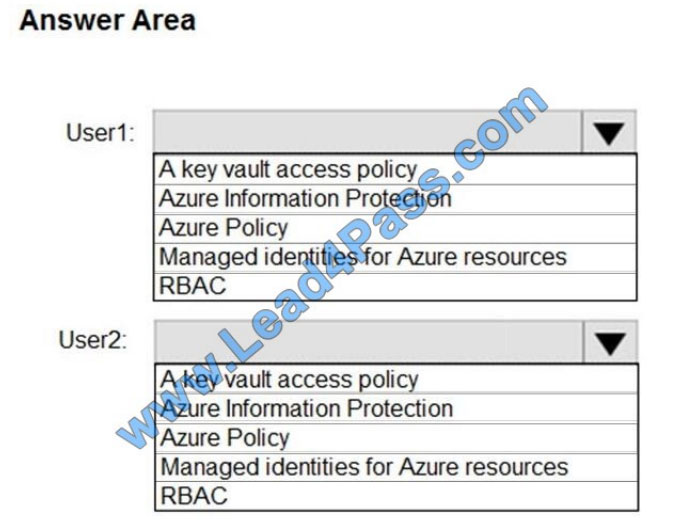
You need to delegate administrative access to the key vault to meet the following requirements:
Provide a user named User1 with the ability to set advanced access policies for the key vault.
Provide a user named User2 with the ability to add and delete certificates in the key vault. Use the principle of least privilege.
What should you use to assign access to each user? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
Hot Area
Correct Answer:
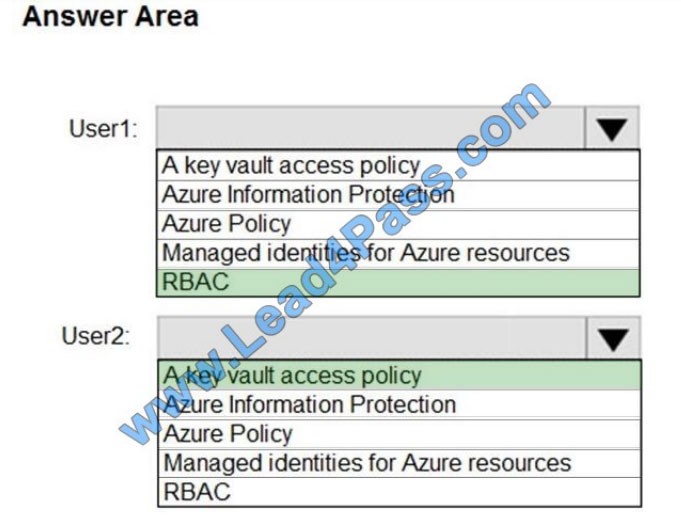
User1: RBAC
RBAC is used as the Key Vault access control mechanism for the management plane. It would allow a user with the
proper identity to:
set Key Vault access policies
create, read, update, and delete key vaults
set Key Vault tags
Note: Role-based access control (RBAC) is a system that provides fine-grained access management of Azure
resources. Using RBAC, you can segregate duties within your team and grant only the amount of access to users that
they need to
perform their jobs.
User2: A key vault access policy
A key vault access policy is the access control mechanism to get access to the key vault data plane. Key Vault access
policies grant permissions separately to keys, secrets, and certificates.
References: https://docs.microsoft.com/en-us/azure/key-vault/key-vault-secure-your-key-vault
QUESTION 4
You need to configure WebApp1 to meet the data and application requirements.
Which two actions should you perform? Each correct answer presents part of the solution. NOTE: Each correct
selection is worth one point.
A. Upload a public certificate.
B. Turn on the HTTPS Only protocol setting.
C. Set the Minimum TLS Version protocol setting to 1.2.
D. Change the pricing tier of the App Service plan.
E. Turn on the Incoming client certificates protocol setting.
Correct Answer: AC
A: To configure Certificates for use in Azure Websites Applications you need to upload a public Certificate.
C: Over time, multiple versions of TLS have been released to mitigate different vulnerabilities. TLS 1.2 is the most
current version available for apps running on Azure App Service. Incorrect Answers:
B: We need to support the Http URL as well. Note: 
References: https://docs.microsoft.com/en-us/azure/app-service/app-service-web-configure-tls-mutual-auth
https://azure.microsoft.com/en-us/updates/app-service-and-functions-hosted-apps-can-now-update-tls-versions/
QUESTION 5
From the Azure portal, you are configuring an Azure policy.
You plan to assign policies that use the DeployIfNotExist, AuditIfNotExist, Append, and Deny effects.
Which effect requires a managed identity for the assignment?
A. AuditIfNotExist
B. Append
C. DeployIfNotExist
D. Deny
Correct Answer: C
When Azure Policy runs the template in the deployIfNotExists policy definition, it does so using a managed identity.
References: https://docs.microsoft.com/bs-latn-ba/azure/governance/policy/how-to/remediate-resources
QUESTION 6
You are configuring an Azure Kubernetes Service (AKS) cluster that will connect to an Azure Container Registry.
You need to use the auto-generated service principal to authenticate to the Azure Container Registry.
What should you create?
A. an Azure Active Directory (Azure AD) group
B. an Azure Active Directory (Azure AD) role assignment
C. an Azure Active Directory (Azure AD) user
D. a secret in Azure Key Vault
Correct Answer: B
When you create an AKS cluster, Azure also creates a service principal to support cluster operability with other Azure
resources. You can use this auto-generated service principal for authentication with an ACR registry. To do so, you
need to create an Azure AD role assignment that grants the cluster\\'s service principal access to the container registry.
References: https://docs.microsoft.com/bs-latn-ba/azure/container-registry/container-registry-auth-aks
QUESTION 7
You need to meet the identity and access requirements for Group1. What should you do?
A. Add a membership rule to Group1.
B. Delete Group1. Create a new group named Group1 that has a membership type of Office 365. Add users and
devices to the group.
C. Modify the membership rule of Group1.
D. Change the membership type of Group1 to Assigned. Create two groups that have dynamic memberships. Add the
new groups to Group1.
Correct Answer: B
Incorrect Answers:
A, C: You can create a dynamic group for devices or for users, but you can\\'t create a rule that contains both users and
devices.
D: For the assigned group you can only add individual members.
Scenario:
Litware identifies the following identity and access requirements: All San Francisco users and their devices must be
members of Group1.
The tenant currently contains this group: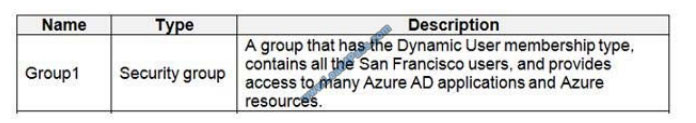
References: https://docs.microsoft.com/en-us/azure/active-directory/users-groups-roles/groups-dynamic-membership
https://docs.microsoft.com/en-us/azure/active-directory/fundamentals/active-directory-groups-create-azure-portal
QUESTION 8
Your network contains an on-premises Active Directory domain named corp.contoso.com.
You have an Azure subscription named Sub1 that is associated to an Azure Active Directory (Azure AD) tenant named
contoso.com.
You sync all on-premises identities to Azure AD.
You need to prevent users who have a given name attribute that starts with TEST from being synced to Azure AD. The solution must minimize administrative effort.
What should you use?
A. Synchronization Rules Editor
B. Web Service Configuration Tool
C. the Azure AD Connect wizard
D. Active Directory Users and Computers
Correct Answer: A
Use the Synchronization Rules Editor and write an attribute-based filtering rule.
References: https://docs.microsoft.com/en-us/azure/active-directory/hybrid/how-to-connect-sync-change-theconfiguration
QUESTION 9
Exhibit tab.)
You are testing an Azure Kubernetes Service (AKS) cluster. The cluster is configured as shown in the exhibit. (Click the
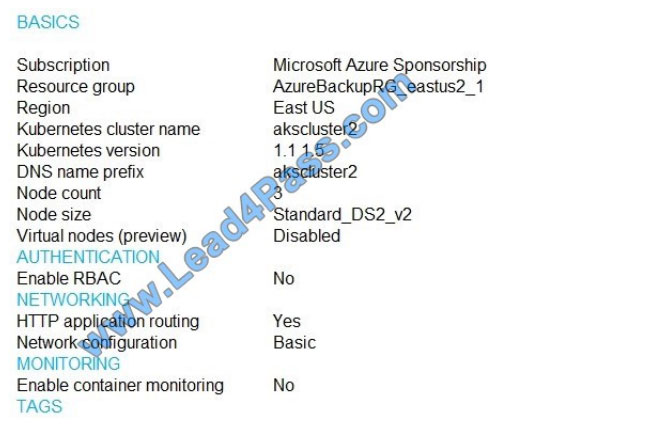
You plan to deploy the cluster to production. You disable HTTP application routing.
You need to implement application routing that will provide reverse proxy and TLS termination for AKS services by using
a single IP address.
What should you do?
A. Create an AKS Ingress controller.
B. Install the container network interface (CNI) plug-in.
C. Create an Azure Standard Load Balancer.
D. Create an Azure Basic Load Balancer.
Correct Answer: A
An ingress controller is a piece of software that provides reverse proxy, configurable traffic routing, and TLS termination
for Kubernetes services.
References: https://docs.microsoft.com/en-us/azure/aks/ingress-tls
QUESTION 10
Your company plans to create separate subscriptions for each department. Each subscription will be associated with the
same Azure Active Directory (Azure AD) tenant.
You need to configure each subscription to have the same role assignments. What should you use?
A. Azure Security Center
B. Azure Policy
C. Azure AD Privileged Identity Management (PIM)
D. Azure Blueprints
Correct Answer: D
Just as a blueprint allows an engineer or an architect to sketch a project\\'s design parameters, Azure Blueprints
enables cloud architects and central information technology groups to define a repeatable set of Azure resources that
implements and adheres to an organization\\'s standards, patterns, and requirements.
Blueprints are a declarative way to orchestrate the deployment of various resource templates and other artifacts such
as: Role Assignments Policy Assignments Azure Resource Manager templates Resource Groups
Reference: https://docs.microsoft.com/en-us/azure/governance/blueprints/overview
QUESTION 11
You have an Azure subscription named Sub1 that contains an Azure Storage account named Contosostorage1 and an
Azure key vault named Contosokeyvault1.
You plan to create an Azure Automation runbook that will rotate the keys of Contosostorage1 and store them in
Contosokeyvault1.
You need to implement prerequisites to ensure that you can implement the runbook.
Which three actions should you perform in sequence? To answer, move the appropriate actions from the list of actions
to the answer area and arrange them in the correct order.
Select and Place:
Correct Answer:
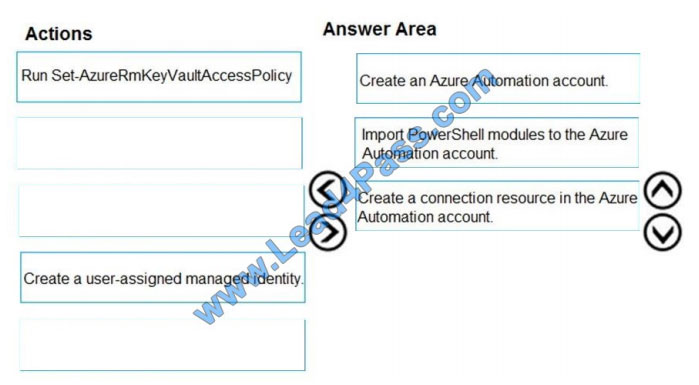
Step 1: Create an Azure Automation account
Runbooks live within the Azure Automation account and can execute PowerShell scripts.
Step 2: Import PowerShell modules to the Azure Automation account
Under `Assets\\' from the Azure Automation account Resources section select `to add in Modules to the runbook. To
execute key vault cmdlets in the runbook, we need to add AzureRM.profile and AzureRM.key vault.
Step 3: Create a connection resource in the Azure Automation account
You can use the sample code below, taken from the AzureAutomationTutorialScript example runbook, to authenticate
using the Run As account to manage Resource Manager resources with your runbooks. The AzureRunAsConnection is a connection asset automatically created when we created `run as accounts\\' above. This can be found under Assets ->
Connections. After the authentication code, run the same code above to get all the keys from the vault.
$connectionName = "AzureRunAsConnection"
try
{
# Get the connection "AzureRunAsConnection "
$servicePrincipalConnection=Get-AutomationConnection -Name $connectionName
"Logging in to Azure..."
Add-AzureRmAccount `
-ServicePrincipal `
-TenantId $servicePrincipalConnection.TenantId `
-ApplicationId $servicePrincipalConnection.ApplicationId `
-CertificateThumbprint $servicePrincipalConnection.CertificateThumbprint
}
References:
https://www.rahulpnath.com/blog/accessing-azure-key-vault-from-azure-runbook/
QUESTION 12
You have an Azure subscription named Sub1 that is associated to an Azure Active Directory (Azure AD) tenant named
contoso.com.
You are assigned the Global administrator role for the tenant. You are responsible for managing Azure Security Center
settings.
You need to create a custom sensitivity label.
What should you do?
A. Create a custom sensitive information type.
B. Elevate access for global administrators in Azure AD.
C. Change Azure Security Center to use Standard-tier-pricing.
D. Enable integration with Microsoft Cloud App Security.
Correct Answer: A
First, you need to create a new sensitive information type because you can\\'t directly modify the default rules.
References: https://docs.microsoft.com/en-us/office365/securitycompliance/customize-a-built-in-sensitive-informationtype
QUESTION 13
Note: This question is part of a series of questions that present the same scenario. Each question in the series contains
a unique solution that might meet the stated goals. Some question sets might have more than one correct solution,
while
others might not have a correct solution.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not
appear on the review screen.
You have an Azure Subscription. The subscription contains 50 virtual machines that run Windows Server 2012 R2 or
Windows Server 2016.
You need to deploy Microsoft Antimalware to the virtual machines.
Solution: You connect to each virtual machine and add a Windows feature.
Does this meet the goal?
A. Yes
B. No
Correct Answer: B
Microsoft Antimalware is deployed as an extension and not a feature.
References: https://docs.microsoft.com/en-us/azure/security/fundamentals/antimalware
Latest leads4pass Microsoft dumps Discount Code 2020

About The leads4pass Dumps Advantage
leads4pass has 7 years of exam experience! A number of professional Microsoft exam experts! Update exam questions throughout the year! The most complete exam questions and answers! The safest buying experience! The greatest free sharing of exam practice questions and answers!
Our goal is to help more people pass the Microsoft exam! Exams are a part of life, but they are important! In the study, you need to sum up the study! Trust leads4pass to help you pass the exam 100%!

Summarize:
This blog shares the latest Microsoft AZ-500 exam dumps, AZ-500 exam questions, and answers! AZ-500 pdf, AZ-500 exam video!
You can also practice the test online! leads4pass is the industry leader!
Select leads4pass AZ-500 exams Pass Microsoft AZ-500 exams "Microsoft Azure Security Technologies". Help you successfully pass the AZ-500 exam.
ps.
Get Microsoft Full Series Exam Dump: https://www.fulldumps.com/?s=microsoft (Updated daily)
Get leads4pass Azure Developer Associate exam dumps: https://www.leads4pass.com/role-based.html
Latest update leads4pass AZ-500 exam dumps: https://www.leads4pass.com/az-500.html (203 Q&As)
[Q1-Q12 PDF] Free Microsoft AZ-500 pdf dumps download from Google Drive: https://drive.google.com/file/d/1zbpomewbVYQK6t2wFwxYtIyde1qhArS6/
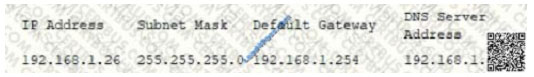 The administrator successfully pings the DNS server from the workstation. Which of the following commands should be
The administrator successfully pings the DNS server from the workstation. Which of the following commands should be