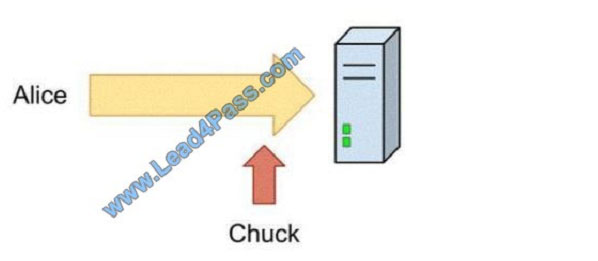
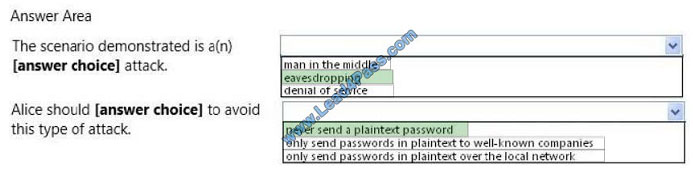
What is the best way to pass the Microsoft 98-388 exam? (First: Exam practice test, Second: leads4pass Microsoft expert.) You can get free Microsoft Java 6 SE 98-388 exam practice test questions here.
Or choose https://www.leads4pass.com/98-388.html (42 Q&As). Study hard to pass the exam easily!
Table of Contents:
- Latest Microsoft Java 6 SE 98-388 google drive
- Effective Microsoft 98-388 exam practice questions
- Related 98-388 Popular Exam resources
- leads4pass Year-round Discount Code
- What are the advantages of leads4pass?
Latest Microsoft Java 6 SE 98-388 google drive
[PDF] Free Microsoft Java 6 SE 98-388 pdf dumps download from Google Drive: https://drive.google.com/open?id=1NZXcF4ZuMIOx-0pr2o193JmmldiSBMvo
98-388: Introduction to Programming Using Java - Microsoft:https://www.microsoft.com/en-us/learning/exam-98-388.aspx
Skills measured
This exam measures your ability to accomplish the technical tasks listed below.
- Understand Java fundamentals (15-20%)
- Work with data types, variables, and expressions (40-45%)
- Implement flow control (15-20%)
- Perform object-oriented programming (10-15%)
- Compile and debug code (5-10%)
Who should take this exam?
Candidates for this exam are application developers working with Java 6 SE or later, secondary and immediate post-secondary level students of software development, or entry-level software developers.
Candidates should have at least 150 hours or instruction or hands-on experience with Java, are familiar with its features and capabilities, and understand how to write, debug and maintain well-formed, well documented Java code.
Latest updates Microsoft 98-388 exam practice questions
QUESTION 1
You are creating a method that converts a string representation of a number into an actual number.
The numbers passed into the method include whole numbers and fractional numbers.
How should you complete the code? To answer, select the appropriate code segments in the answer area.
NOTE: Each correct selection is worth one point.
Hot Area: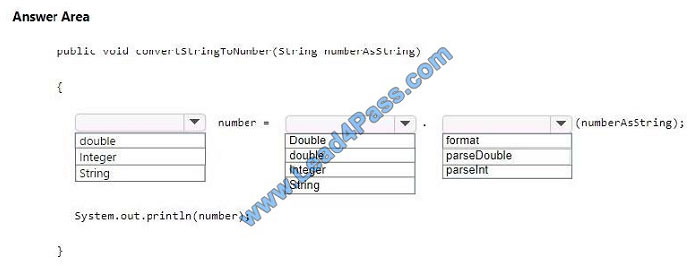
Correct Answer:
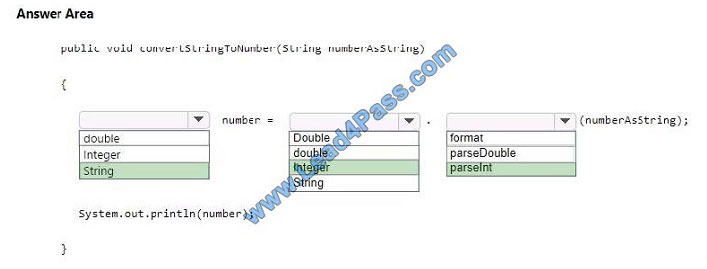
References: https://docs.oracle.com/javase/tutorial/java/data/converting.html
QUESTION 2
You have a Java class named InsurancePolicy.
You need to define a constant data member named RATE. The data member must be accessible by any class without
instantiating the InsurancePolicy class.
How should you complete the code? To answer, drag the appropriate code segment to the correct position. Each code
segment may be used once, more than once, or not at all. You may need to drag the split bar between panes or scroll
to
view content.
NOTE: Each correct selection is worth one point.
Select and Place: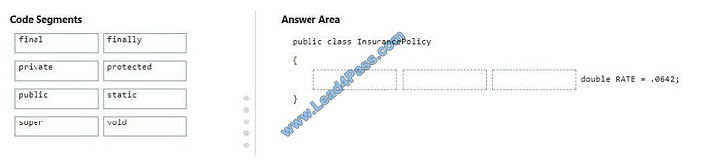
Correct Answer:

References: https://docs.oracle.com/javase/tutorial/java/javaOO/classvars.html
QUESTION 3
You are interviewing for a job at Adventure Works, Inc. The hiring manager asks you to create a single console
program.
The program takes multiple arguments from the command line and writes them to the screen in the same order as they
were typed on the command line.
Which three code segments should you use to develop the solution? To answer, move the appropriate code segments
from the list of code segments to the answer area and arrange them in the correct order.
Select and Place: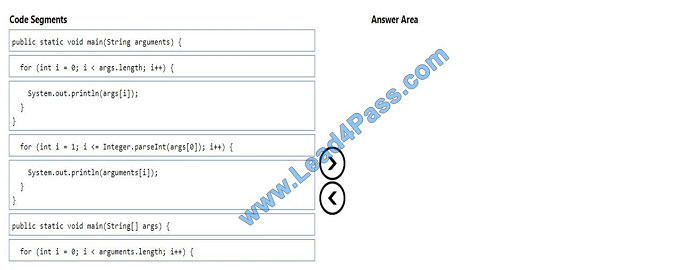
Correct Answer:
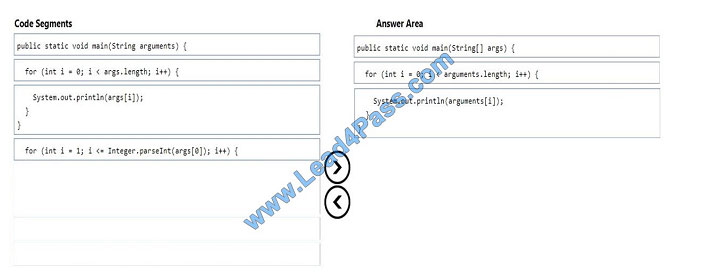
References: https://docs.oracle.com/javase/tutorial/getStarted/cupojava/netbeans.html
QUESTION 4
You are creating a method that processes invoices. The invoices are contained in an ArrayList instance. After each
invoice is processed, the method must remove the invoice from the ArrayList instance.
How should you complete the code? To answer, select the appropriate code segments in the answer area.
NOTE: Each correct selection is worth one point.
Hot Area: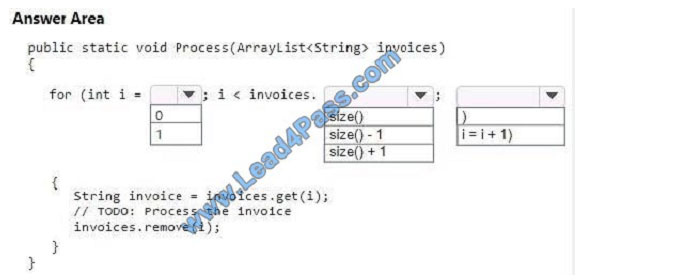
Correct Answer:
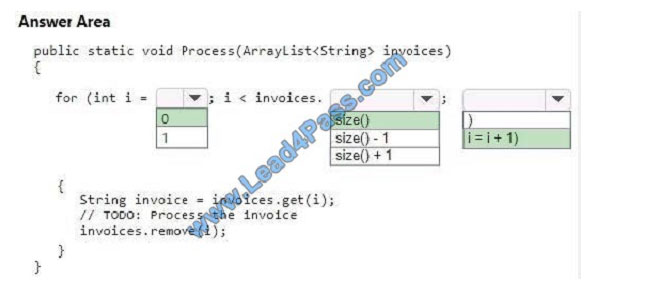
References: https://beginnersbook.com/2013/12/java-arraylist/
QUESTION 5
You need to analyze the following code segment. Line numbers are included for reference only.
What is the output of line 12 when you run printInt()?
A. 0
B. 1
C. 2
D. 3
Correct Answer: A
QUESTION 6
You need to evaluate the following Java program. Line numbers are included for reference only.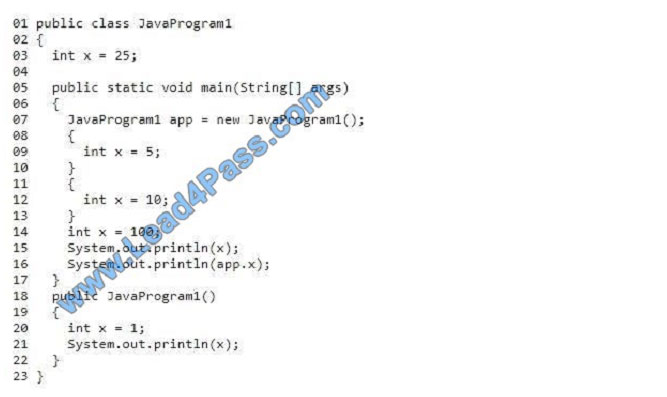
Which three values will be displayed in sequence? To answer, move the appropriate values from the list of values to the
answer area and arrange them in the correct order. NOTE: Each correct selection is worth one point.
Select and Place:
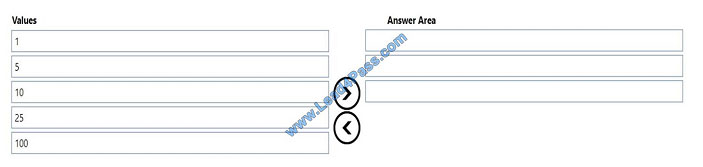
Correct Answer:
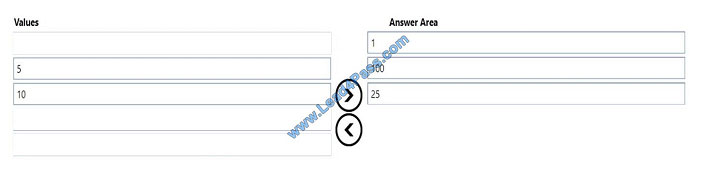
QUESTION 7
You work as a Java programmer. A member of the team creates the following program. Line numbers are included for
reference only.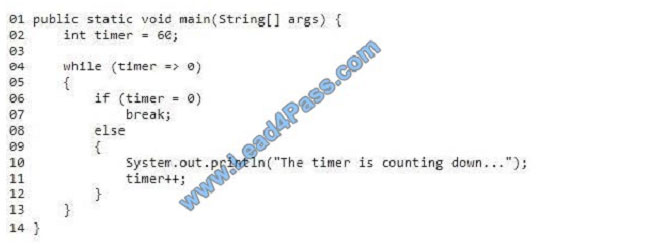
The program is supposed to display a message to the console while it counts down from 60. The method does not work
as intended.
How should you complete the code? To answer, select the appropriate code segments in the answer area.
NOTE: Each correct selection is worth one point.
Hot Area:
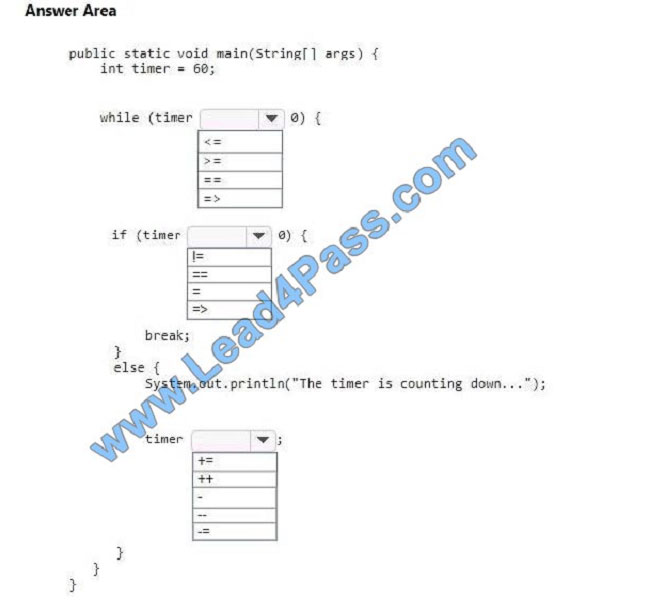
Correct Answer:

References: https://docs.oracle.com/javase/tutorial/java/nutsandbolts/operators.html
QUESTION 8
Traders hires you to write a Java program to manage account openings. To open a new account, a user must meet one
the following requirements:
be over 65 years old and have a minimum annual income of 10,000
be at least 21 and have an annual income greater than 25,000
How should you complete the code? To answer, drag the appropriate operator to the correct position. Each operator
may be used once, more than once, or not at all. You may need to drag the split bar between panes or scroll to view
content.
NOTE: Each correct selection is worth one point.
Select and Place: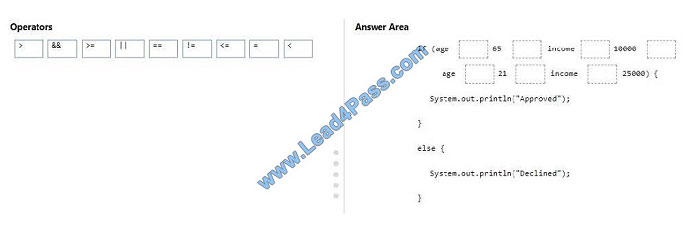
Correct Answer:
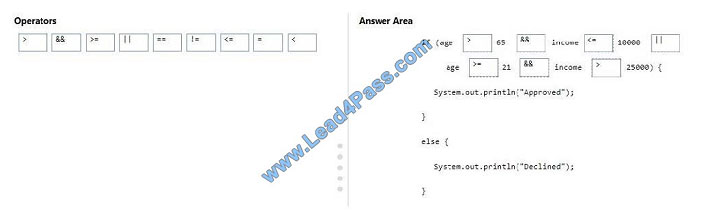
References: https://www.tutorialspoint.com/java/java_basic_operators.htm
QUESTION 9
You are writing a Java console program. The program accepts command line arguments.
You need to ensure that the main method parses and handles each command line argument.
How should you complete the code? To answer, select the appropriate code segments in the answer area.
NOTE: Each correct selection is worth one point.
Hot Area: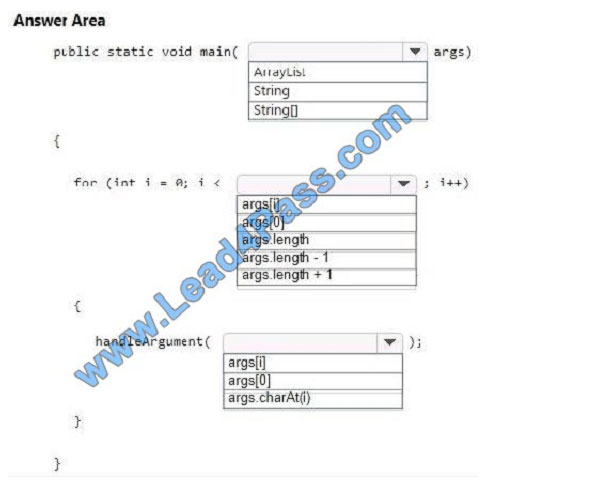
Correct Answer:
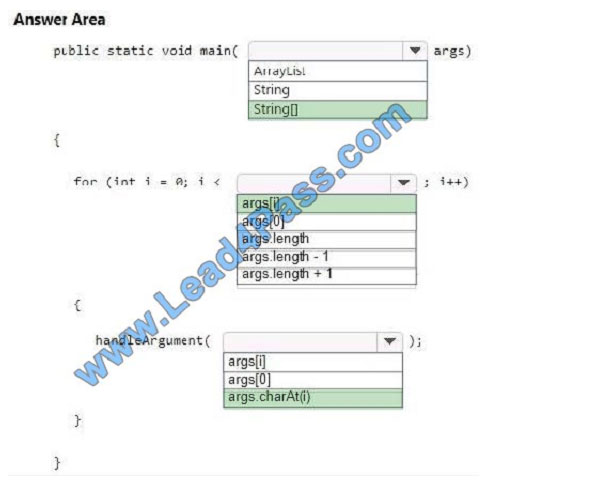
QUESTION 10
You are interviewing for a job as a Java developer.
You are presented with the following code. Line numbers are included for reference only.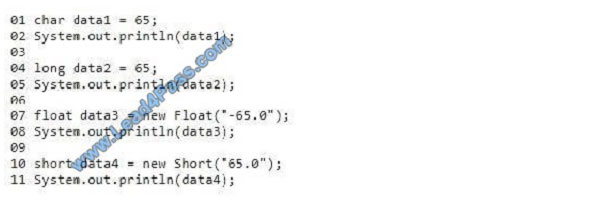
You need to evaluate what happens when the code runs.
Use the drop-down menus to select the answer choice that answers each question based on the information presented
in the code.
NOTE: Each correct selection is worth one point.
Hot Area:

Correct Answer:

QUESTION 11
You need to evaluate the following code. Line numbers are included for reference only.
Use the drop-down menus to select the answer choice that answers each question based on the information presented
in the code. NOTE: Each correct selection is worth one point.
Hot Area:
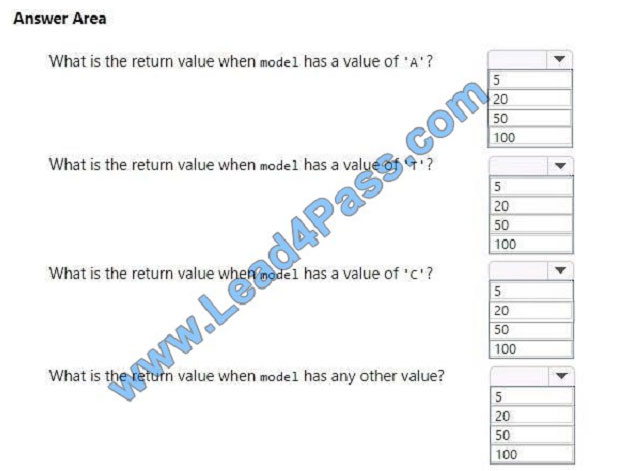
Correct Answer:
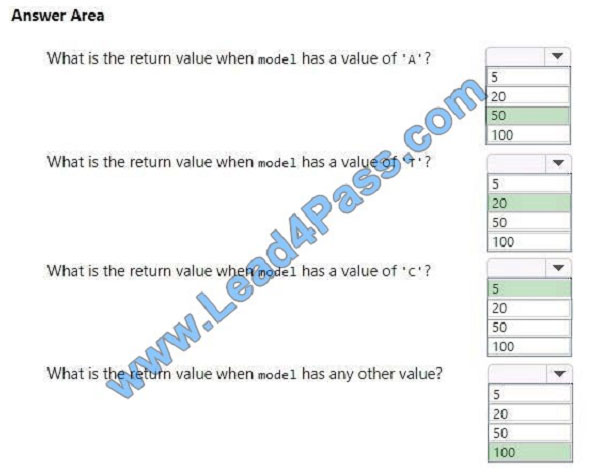
QUESTION 12
You attend an interview for a job as a Java programmer.
You need to declare a two by three array of the double type with initial values.
How should you complete the code? To answer, drag the appropriate code segment to the correct location. Each code
segment may be used once, more than once, or not at all. You may need to drag the split bar between panes or scroll to
view content.
NOTE: Each correct selection is worth one point.
Select and Place:
Correct Answer:

QUESTION 13
You write the following Java program for Munson
Correct Answer: 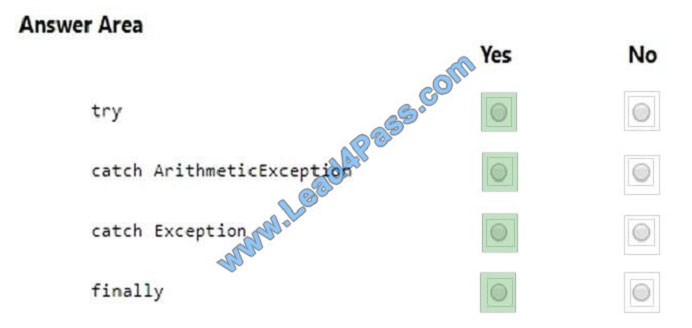
References: https://www.w3schools.com/java/java_try_catch.asp
Related 98-388 Popular Exam resources
| title | youtube | Microsoft | leads4pass | leads4pass Total Questions | |
|---|---|---|---|---|---|
| Microsoft Java 6 SE | leads4pass 98-388 dumps pdf | leads4pass 98-388youtube | 98-388: Introduction to Programming Using Java - Microsoft | https://www.leads4pass.com/98-388.html | 42 Q&A |
leads4pass Year-round Discount Code

What are the advantages of leads4pass?
leads4pass employs the most authoritative exam specialists from Microsoft, Cisco, CompTIA, IBM, EMC, etc. We update exam data throughout the year. Highest pass rate! We have a large user base. We are an industry leader! Choose leads4pass to pass the exam with ease!

Summarize:
It's not easy to pass the Microsoft 98-388 exam, but with accurate learning materials and proper practice, you can crack the exam with excellent results. leads4pass.com provides you with the most relevant learning materials that you can use to help you prepare.