Latest updates Cisco CCDP Designing Cisco Network Service Architectures (ARCH v3.0) 300-320 exam questions and Answers! Free sharing 300-320 pdf online download, online exam Practice test, easy to improve skills! Get the full 300-320 exam dumps: https://www.leads4pass.com/300-320.html (Total questions:600 Q&A). Year-round updates! guarantee the first attempt to pass the exam!
[PDF] Free Cisco 300-320 pdf dumps download from Google Drive: https://drive.google.com/open?id=1CO03i-baRPjHkU54CVGIIfaTH2icYbXh
[PDF] Free Full Cisco pdf dumps download from Google Drive: https://drive.google.com/open?id=1CMo2G21nPLf7ZmI-3_hBpr4GDKRQWrGx
300-320 ARCH - Cisco: https://www.cisco.com/c/en/us/training-events/training-certifications/exams/current-list/arch-300-320.html
Latest effective Cisco 300-320 Exam Practice Tests
QUESTION 1
When designing data centers for multitenancy, which two benefits are provided by the implementation of VSAN and
zoning? (choose two)
A. VSAN provides a means of restricting visibility and connectivity among devices connected to a zone
B. VSANs have their own set of services and address space, which prevents an issue in one VSAN from affecting
others
C. Zones provide the ability to create many logical SAN fabrics on a single Cisco MDS 9100 family switch
D. VSANs and zones use separate fabrics
E. Zones allow an administrator to control which initiators can see which targets
Correct Answer: DE
QUESTION 2
While configuring a QoS policy, analysis of the switching infrastructure indicates that the switches support 1P3Q3T
egress queuing. Which option describes the egress queuing in the infrastructure?
A. The threshold configuration allows for inter-queue QoS by utilizing buffers.
B. The priority queue must contain real-time traffic and network management traffic.
C. The 1P3Q3T indicates one priority queue, three standard queues, and three thresholds.
D. The priority queue should use less than 20% of the total bandwidth.
Correct Answer: B
QUESTION 3
Which three authentication services are supported by Cisco NAC Appliance? (Choose three.)
A. RADIUS
B. LDAP
C. Kerberos
D. TACACS+
E. local
F. SNMP
Correct Answer: ABC
Working with Existing Backend Authentication Servers When working with existing backend authentication servers,
Cisco supports the following authentication protocol types:
Kerberos
RADIUS (Remote Authentication Dial-In User Service)
Windows NT (NTLM Auth Server)
LDAP (Lightweight Directory Access Protocol)
https://www.cisco.com/c/en/us/td/docs/security/nac/appliance/configuration_guide/47/cam/ 47cam-book/m_auth.html
QUESTION 4
Design for data center where you don\\'t have to dedicate one switch per rack?
A. Top of rack
B. End of row
C. Blade Switch
D. Middle of row
Correct Answer: B
QUESTION 5
Cisco FabricPath brings the benefits of routing protocols to Layer 2 network Ethernet environments. What are two
advantages of using Cisco FabricPath technology? (Choose two)
A. Cisco FabricPath relies on OSPF to support Layer 2 forwarding between switches, which allows load balancing
between redundant paths.
B. Cisco FabricPath provides MAC address scalability with conversational learning.
C. Loop mitigation is provided by the TTL field in the frame.
D. Cisco FabricPath is IETF-standard and is not used with Cisco products.
E. Cisco FabricPath technology is supported in all Cisco platforms and can replace legacy Ethernet in all campus
networks.
Correct Answer: BC
QUESTION 6
Which four primary attributes define a WAN service? (Choose four.)
A. bandwidth
B. bursting capacity
C. memory
D. CPU
E. QoS classes and policies
F. latency
G. multicast support
Correct Answer: ABEG
QUESTION 7
Which command can you enter to inject BGP routes into an IGP?
A. redistribute bgp
B. redistribute static
C. redistribute static subnet
D. default-information originate
Correct Answer: A
QUESTION 8
Refer to the exhibit.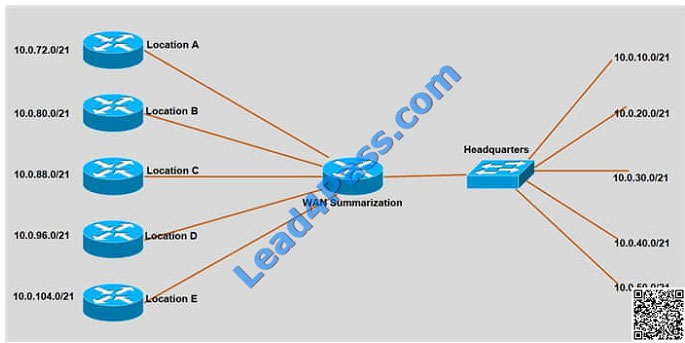 An engineer must apply IP addressing to five new WAN sites and choses the new subnets pictured. The previous
An engineer must apply IP addressing to five new WAN sites and choses the new subnets pictured. The previous
administrator applied the addressing at Headquarters. Whitch option is the minimum summary range to cover the
existing WAN sites while also allowing for three additional WAN sites of the same size, for future growth?
A. 10.0.60.0/18
B. 10.0.64.0/21
C. 10.0.64.0/17
D. 10.0.0.0/17
E. 10.0.64.0/18
Correct Answer: E
QUESTION 9
What QoS technology allows traffic to pass even though it has exceeded the bandwidth limit but will be queued later?
A. Shaping
B. Policing
C. Weighted Fair Queuing
D. Low Latency Queuing
Correct Answer: A
QUESTION 10
An engineer is redesigning the infrastructure for a campus environment. The engineer must maximize the use of the
links between the core and distribution layers. By which two methods can this usage be maximized? (Choose two.)
A. Design the links between the core and distribution layers to use RPVSTP+
B. Design with multiple unequal-cost links between the core and distribution layers.
C. Design the links between the core and distribution layers to use an IGP
D. Design the links between the core and distribution layers to use HSRP.
E. Design with multiple equal-cost links between the core and distribution layers.
Correct Answer: AD
QUESTION 11
An CSPF router should have a maximum of how many adjacent neighbors?
A. 80
B. 60
C. 100
D. 50
Correct Answer: B
QUESTION 12
DRAG DROP
Drag and Drop question with regards to Cisco Application-Centric Infrastructure ACI .
Select and Place: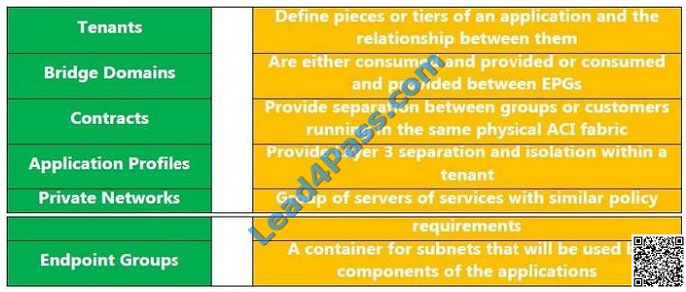
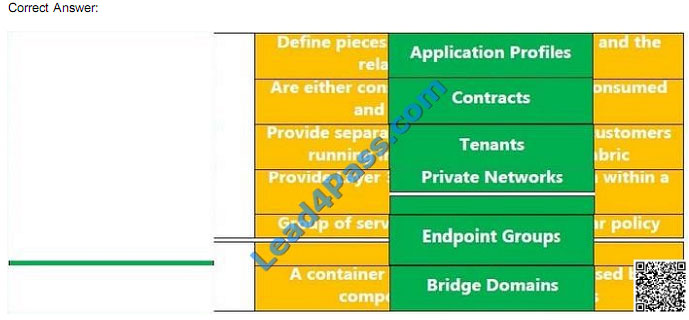
QUESTION 13
What is the preferred protocol for a router that is running an IPv4 and IPv6 dual stack configuration?
A. IPX
B. microsoft Netbios
C. IPv6
D. IPv4
Correct Answer: C
QUESTION 14
Which one of these could you implement to sustain a large DDoS attack?
A. Stateful firewall
B. uRPF
C. Connections limits and timeouts
D. Access-lists
Correct Answer: C
QUESTION 15
Which statement about Fibre Channel communications is correct?
A. N_Port to N_Port connections use logical node connection points.
B. Flow control is only provided by QoS.
C. It must be implemented in an arbitrated loop.
D. Communication methods are similar to those of an Ethernet bus.
Correct Answer: A
Fibre Channel supports a logical node connection point between node ports (N_ports). This is similar to TCP and UDP
sockets.
QUESTION 16
What location are security policies enforced in ACI?
A. End Point
B. Spine
C. Leaf
D. APIC
Correct Answer: C
QUESTION 17
L2 extention through IP in the data center (MAC-in-IP)
A. fiberpath
B. TRILL
C. OTV
D. Vxlan
Correct Answer: C
QUESTION 18
What is an advantage of having an out-of-band management?
A. It is less expensive to have an out-of-band management.
B. Network devices can still be managed, even in case of network outage.
C. There is no separation between the production network and the management network.
D. SSH protocol must be used to manage network devices.
Correct Answer: B
QUESTION 19
Which two of these are characteristics of multicast routing? (Choose two.)
A. multicast routing uses RPF.
B. multicast routing is connectionless.
C. In multicast routing, the source of a packet is known.
D. When network topologies change, multicast distribution trees are not rebuilt, but use the original path
E. Multicast routing is much like unicast routing, with the only difference being that it has a a group of receivers rather
than just one destination
Correct Answer: AC
QUESTION 20
Which statement about the ToR design model is true?
A. It can shorten cable runs and simplify rack connectivity.
B. Each ToR switch must be individually managed.
C. Multiple ToR switches can be interconnected to provide a loop-free spanning-tree infrastructure.
D. It can connect servers that are located in separate racks.
Correct Answer: A
QUESTION 21
Which Cisco feature can be run on a Cisco router that terminates a WAN connection, to gather and provide WAN circuit
information that helps switchover to dynamically back up the WAN circuit?
A. Cisco Express Forwarding
B. IP SLA
C. passive interface
D. traffic shaping
Correct Answer: B
QUESTION 22
A company needs to configure a new firewall and have only one public IP address to use in this firewall. The engineer
need to configure the firewall with NAT to handle inbound traffic to the mail server in addition to internet outbound
traffic. Which options could he use ? (Choose Two)
Which options could he use ? (Choose Two)
A. Static NAT for inbound traffic on port 25
B. Dynamic NAT for outbound traffic
C. Static NAT for outbound traffic on port 25
D. Dynamic NAT for inbound traffic
E. NAT overload for outbound traffic
F. NAT overload for inboud traffic on port 25
Correct Answer: AE
QUESTION 23
Which two key components are related to one firewall per ISP design option for e-commerce? (Choose two.)
A. It is a common approach to single-homing.
B. This approach is commonly used in large sites.
C. Any failure on an edge router results in a loss of session.
D. It has one NAT to two ISP-assigned blocks.
E. It is difficult to set up and administer.
Correct Answer: CD
QUESTION 24
Which technology should a network designer combine with VSS to ensure a loop free topology with optimal
convergence time?
A. Portfast
B. UplinkFast
C. RPVST +
D. Mulitchassis EtherChannel
Correct Answer: D
QUESTION 25
A Network administrator want to increase the security level in the core layer and want to confirm that the users that have
their default GW on an interface in the core switch can access specific networks and can\\'t access the remaining
networks.
Which feature can help him to achieve this?
A. vlan access control list
B. https://www.leads4pass.com/300-320.html
C. https://www.leads4pass.com/300-320.html
D. https://www.leads4pass.com/300-320.html
Correct Answer: A
QUESTION 26
A company have single ASA hardware box and they need to separate company departments in way that they can apply
different rules on them, ACL, NAT, and so on... Which mode is needed?
A. routed mode
B. transparent mode
C. multiple context mode
D. active failover mode
Correct Answer: C
QUESTION 27
` the rule on the left to match the appropriate activity on the right.
Select and Place: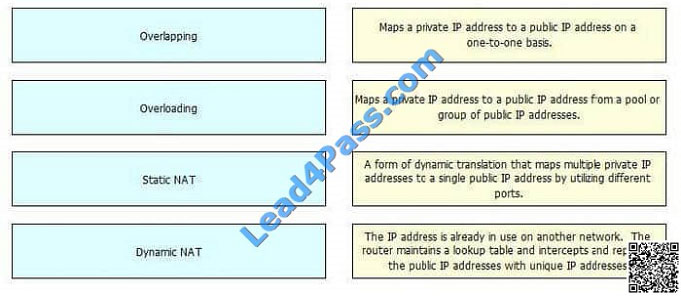 Correct Answer:
Correct Answer: 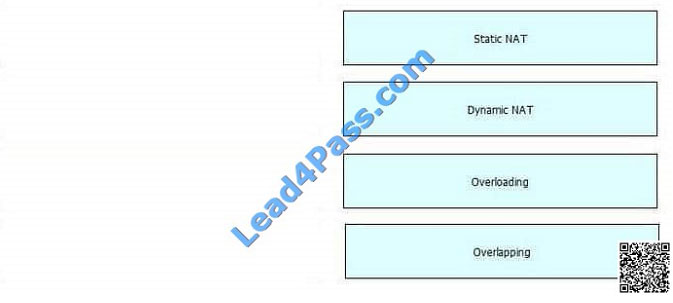
QUESTION 28
DRAG DROP
Select and Place: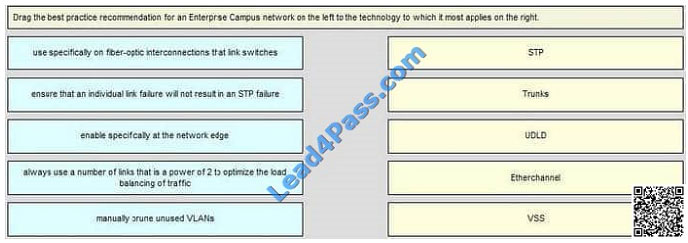 Correct Answer:
Correct Answer: 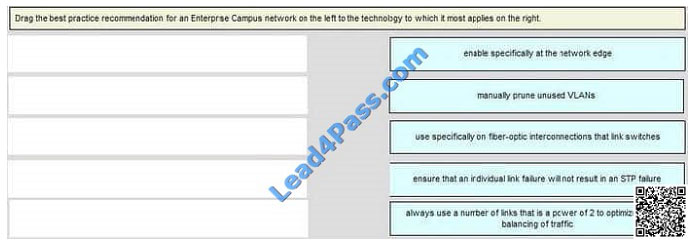 Enable specifically at the network edge >STP Manually prune unused VLANs >Trunks Use specifically on fiber-optic
Enable specifically at the network edge >STP Manually prune unused VLANs >Trunks Use specifically on fiber-optic
interconnections that link switches >UDLD Ensure that an individual link failure will not result in an STP failure
>Etherchannel Always use a number of links that is a power of 2 (2, 4, 8) to optimize the load balancing of traffic> VSS
QUESTION 29
A network design engineer has been asked to reduce the size of the SPT on an IS-IS broadcast network. Which option
should the engineer recommend to accomplish this task?
A. Configure the links as point-to-multipoint.
B. Configure QoS in all links.
C. Configure a new NET address.
D. Configure the links as point-to-point.
Correct Answer: D
QUESTION 30
An engineer is designing a multi cluster bgp network, each cluster has 2 RRs and 4 RR clients which 2 options must be
considered?
A. Clients from all clusters should peer with all RRs
B. All route reflectors should be non client peers and topology partially meshed
C. All RRs must be non client peers in a fully meshed topology
D. Clients must not peer with IBGP speakers outside the client router
E. Clients should peer with at least one other client outside it\\'s cluster
Correct Answer: DE
Route reflectors must still be fully IBGP meshed with nonclients. Therefore, route reflectors reduce meshing within
clusters, but all mesh links outside the cluster must be maintained on the route reflector. The route reflector clients get
information from IBGP speakers outside the cluster via the route reflector.
QUESTION 31
What is an advantage of using the VPC feature in data center environment ?
A. All available uplinks bandwidth is used.
B. FHRP is not required
C. A single IP is used for management of both devices
D. The two switches form a single control plane
Correct Answer: A
QUESTION 32
What command essentially turns on auto summarization for EIGRP?
A. area 0 range 10.0.0.0 255.0.0.0.0
B. router eigrp 1
C. ip summary-address eigrp 1 10.0.0.0 255.0.0.0
D. ip summary-address 10.0.0.0 255.0.0.0
E. eigrp stub
Correct Answer: B
QUESTION 33
An engineer has an implemented a QOS architecture that requires a signaling protocol to tell routers which flows of
packets require special treatment. Which two mechanisms are important to establish and maintaining QOS
architecture? (choose two)
A. classification
B. tagging
C. packet scheduling
D. admission control
E. resource reservation
Correct Answer: DE
QUESTION 34
A customer with a single Cisco Adaptive Security Appliance wants to separate multiple segments of the e-commerce
network to allow for different security policies. What firewall technology accommodates these design requirements?
A. Routed mode
B. Virtual-context
C. Transparent mode
D. Virtual private network
E. private VLANs
F. admission control
Correct Answer: B
QUESTION 35
OTV to interconnect three data centers and what should there be in each data center
A. VTEP
B. vxlan ?
Correct Answer: A
QUESTION 36
A customer requires resiliency and availability for applications hosted in the data center. What two technologies meet
this requirement? (Choose two)
A. SLB
B. LTM
C. GLBP
D. GTM
E. HSRP
Correct Answer: BD
QUESTION 37
Which option prevents the dropping of asymmetrically routed packets in active/active failover paired firewalls?
A. Nothing can be done to prevent this from happening.
B. Configure different policies on both firewalls.
C. Assign similar interfaces on each firewall to the same asymmetric routing group.
D. Assign similar interfaces on each firewall to a different asymmetric routing group.
Correct Answer: C
QUESTION 38
Which two options regarding the Cisco TrustSec Security Group Tag are true? (Choose two)
A. It is assigned by the Cisco ISE to the user or endpoint session upon login
B. Best practice dictates it should be statically created on the switch
C. It is removed by the Cisco ISE before reaching the endpoint.
D. Best Practice dictates that deployments should include a guest group allowing access to minimal services
E. Best Practice dictates that deployments should include a security group for common services such as DNS and
DHCP
Correct Answer: AE
QUESTION 39
In which OSI layer does IS-IS operate?
A. Layer 1
B. Layer 2
C. Layer 3
D. Layer 4
Correct Answer: B
QUESTION 40
When is a first-hop redundancy protocol needed in the distribution layer?
A. when the design implements Layer 2 between the access and distribution blocks
B. when multiple vendor devices need to be supported
C. when preempt tuning of the default gateway is needed
D. when a robust method of backing up the default gateway is needed
E. when the design implements Layer 2 between the access switch and the distribution blocks
Correct Answer: A
This is the latest update released by the Cisco CCDP Designing Cisco Network Service Architectures (ARCH v3.0) 300-320 exam questions and answers,and we share 40 exam questions and answers for free to help you improve your skills! You can download 300-320 pdf or watch the 300-320 YouTube video tutorial online! Get the full 300-320 exam dumps: https://www.leads4pass.com/300-320.html (Total questions:600 Q&A). Help you pass the exam quickly!
[PDF] Free Cisco 300-320 pdf dumps download from Google Drive: https://drive.google.com/open?id=1CO03i-baRPjHkU54CVGIIfaTH2icYbXh
[PDF] Free Full Cisco pdf dumps download from Google Drive: https://drive.google.com/open?id=1CMo2G21nPLf7ZmI-3_hBpr4GDKRQWrGx
leads4pass Promo Code 12% Off

We share more practical and effective exam dumps (Cisco,Microsoft,Oracle,Citrix,Comptia…) The latest citrix cce-v 1y0-401 exam dumps help you improve your skills
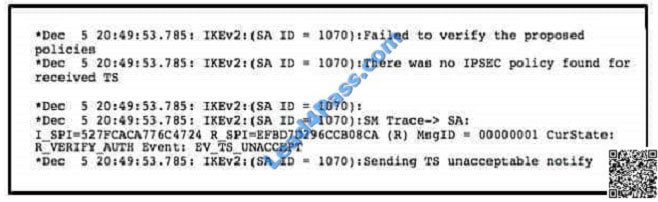 A. incorrect PSK
A. incorrect PSK