What is the best Cisco 400-201 dumps exam materias? Prepare for Cisco 400-201 exam test with high quality Cisco CCIE Service Provider 400-201 dumps exam practice questions and answers download free try. The best and most updated Cisco CCIE Service Provider 400-201 dumps pdf materials and vce youtube demo free shared. "CCIE Service Provider Written Exam Version 4.1" is the name of Cisco CCIE Service Provider https://www.leads4pass.com/400-201.html exam dumps which covers all the knowledge points of the real Cisco exam. Useful latest Cisco CCIE Service Provider 400-201 dumps pdf training resources and study guides free download, pass Cisco 400-201 exam quickly and easily at first attempt.
Latest Cisco 400-201 dumps pdf materials free download: https://drive.google.com/open?id=0B_7qiYkH83VRanpER0JENHVtUGM
Latest Cisco 400-101 dumps pdf materials free download: https://drive.google.com/open?id=0B_7qiYkH83VRQ1BCdmJuZzdZN0U
Best Cisco CCIE Service Provider 400-201 dumps exam questions and answers (1-20)
QUESTION 1
What three major tasks are performed by a Designated Intermediate System in an ISIS pseudonode environment? (Choose three.)
A. updating the pseudonode LSP
B. maintaining pseudonode link-state information
C. creating the pseudonode LSP
D. flooding LSPs over the LAN
E. election of the pseudonode
Correct Answer: ACD
QUESTION 2
Two routers that are running MPLS and LDP have multiple links that than connect them to each other. Anengineer wants to ensure that the label bindings are not flushed from the LIB if one of the links fails. Which configuration meets this requirement?
A. the mpls ldp neighbor targeted command
B. the mpls ip command on a Cisco MPLS TE tunnel
C. the mpls ldp discovery targeted-hello accept command
D. the mpls ldp session protection command
Correct Answer: D
QUESTION 3
Refer to the exhibit.
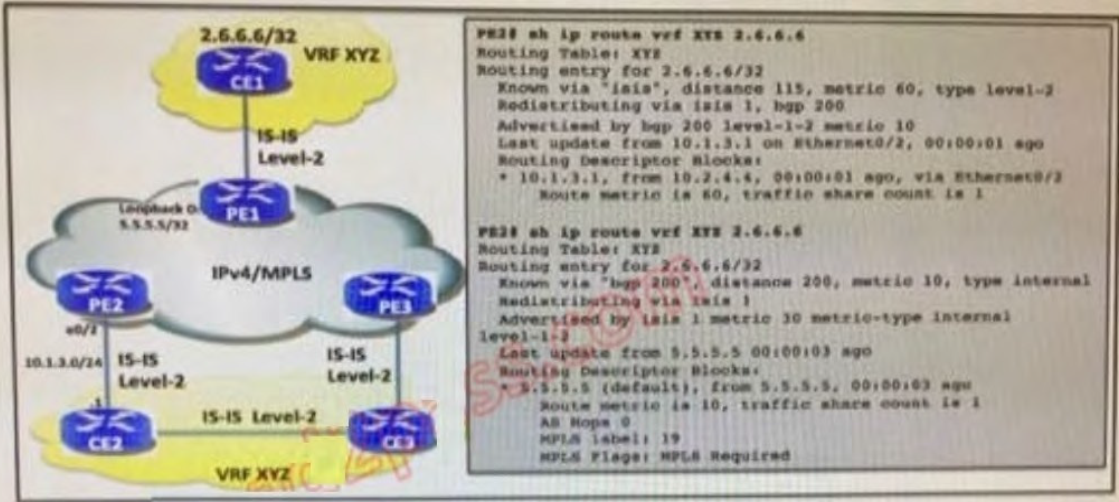
The 2.6.6.6/32 prefix is flapping when PE1 is flapping. Which action can fix this issue?
A. On PE2, allow only redistribution from BGP into IS-IS; on PE3, allow only redistribution from IS-OS into BGP.
B. Configure all IS-IS instances as level-1-only.
C. Configure a sham link between PE2 and PE3.
D. On PE2 and PE3, reconfigure redistribute BGP into IS-IS using the metric-type external parameter.
Correct Answer: D
QUESTION 4
Refer to the exhibit.
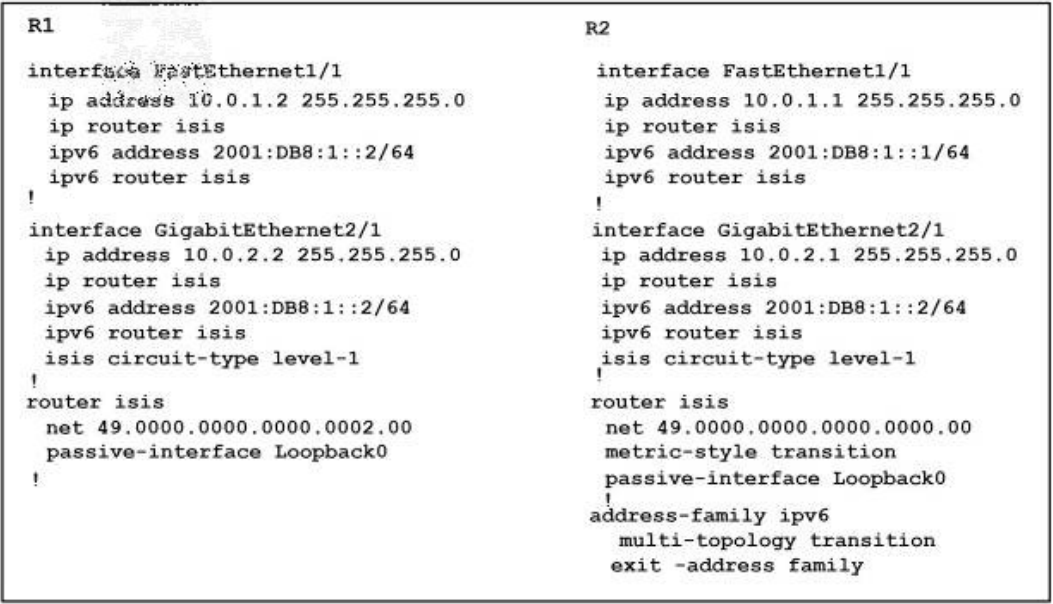
When a traceroute is performed from a PC behind R2, the next hop on R1 for IPv4 is 10.0.1.2, and for IPv6 it is 2001:DB8:2:2. What is causing thus behavior? 400-201 dumps
A. GigabitEthernet2/1 has a Level 1-only adjacency. This causes it to be the preferred path for the IPv6 packets.
B. When SPF ran on R2, it calculated two equal paths to R1. It was a coincidence that than the packets choose different paths.
C. Multitopology is enabled on R2, which causes the IPv6 packets to use a different path than the IPv4 packets.
D. 2001:DB8:2::2 is on a Gigabit Ethernet interface. Because its speed is higher than Fast Ethernet, the IS-IS metric is preferred.
Correct Answer: C
QUESTION 5
Refer to the exhibit.

Which MPLS TE component keeps track of the flooding and admission control?
A. MPLS TE priorities
B. RSVP
C. link attributes
D. link manager
Correct Answer: D
QUESTION 6
Which is the main goal of BGPsec regards to improve BGP security?
A. Reduces risk of improper route propagation from unauthorized AS numbers
B. Configures BGP route verification by storing routes in a database used to validate AS numbers
C. Adds encryption to route propagation outside the iBGP AS
D. Increases legitimacy and authenticity of BGP advertisements
Correct Answer: D
QUESTION 7
Which two models are used in MPLS TE bandwidth constraints? (Choose two)
A. mdm
B. rdm
C. bdm
D. mam
E. tern
Correct Answer: BD
QUESTION 8
In a typical three-node OpenStack deployment, which two components are part of the controller node? (Choose two)
A. Neutron Layer 3 agent
B. Neutron DHCP agent
C. Identity Service
D. Neutron Layer 2 agent
Correct Answer: AD
QUESTION 9
What are the two benefits of graceful restart? (Choose two)
A. Graceful restart allows session information recovery without disruption to the network.
B. A node can perform a graceful restart to help a neighbor recover its state. The label bindings are kept on state information, which helps the failed node recover faster and does not affect the current forward traffic.
C. Graceful restart allows a node to recover state from its neighbor when there is no RP or before the device undergoes SSO.
D. Graceful restart does not allow session information recovery.
E. During a graceful restart, the router removes any stale prefixes after a timer for stale entries expires
Correct Answer: AB
QUESTION 10
Which three statements about the BGP next-hop attribute are true? (Choose three.)
A. EBGP sessions between confederation sub ASs do not modify the next-hop attribute.
B. By default, iBGP sessions change the next-hop attribute learned from eBGP peers to self address.
C. By default, the next-hop attribute is not changed when a prefix is reflected by the route reflector
D. EBGP sessions between confederation sub ASs change the next-hop attribute to peer address.
E. By default, iBGP sessions preserve the next-hop attribute learned from eBGP peers.
Correct Answer: ACE
QUESTION 11
A network engineer is responsible for implementing a solution with Cisco IOS XR Software that ensures continuous forwarding during a control plane failure. Which two technologies should the engineer consider? 400-201 dumps (Choose two.)
A. IP FRR
B. NSR
C. graceful restart
D. BFD
E. TE FRR
Correct Answer: BC
QUESTION 12
The Attribute field within the IS-IS LSP header contains which of the following flags? (Choose four)
A. IS-Type
B. Overload (LSPDBOL)
C. Pseudonode (PN)
D. Attached (ATT)
E. Fragment (Frag-Nr)
F. Partition (P)
Correct Answer: ABDF
QUESTION 13
One ISP has hundreds of routers that run IS-IS, you want to redesign the network to improve performance and convergence, which are correct ways? (Choose two)
A. Bidirectional forwarding failure detection
B. tuning of SPF PRC and LSP.......exp backoff timers C. IS-IS fast flooding of LSPs
C. IP Event Dampending
D. tuning of IS-IS hello parameters
Correct Answer: BC
QUESTION 14
Refer to the exhibit.
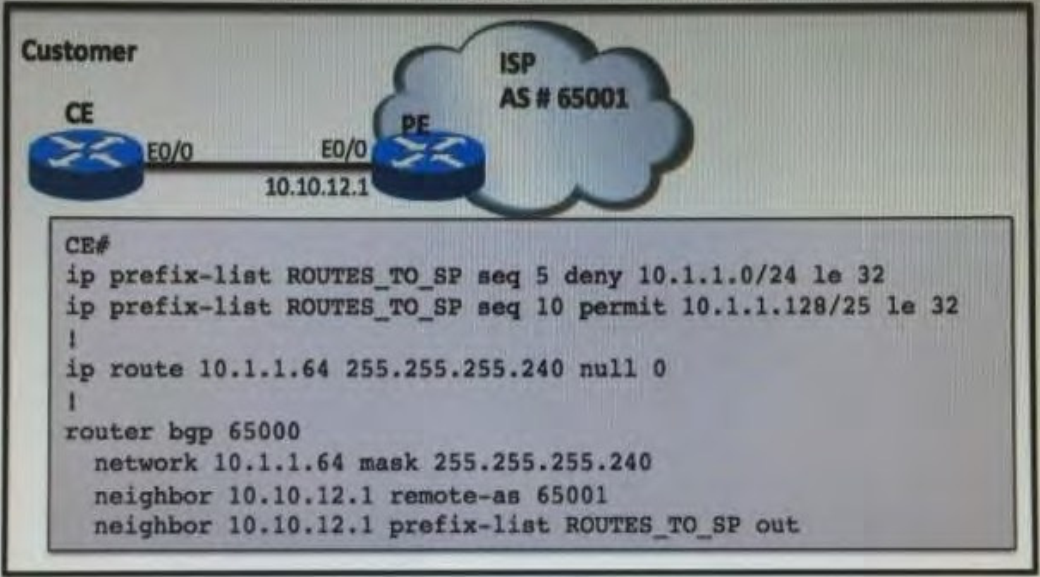
The prefix 10.1.1.64/28 should be advertised to the PE router, yet the prefix is not being received by the PE. Which configuration should be applied on CE in order to fix this issue?
A. ip prefix-list ROUTES_TO_SP seq 1 permit 10.1.1.64/28
B. router bgp 65000no network 10.1.1.64 mask 255.255.255.240 network 10.1.1.128 mask 255.255.255.128
C. ip prefix-list ROUTES_TO_SP permit 10.1.1.64/28
D. router bgp 65000no network 10.1.1.64 mask 255.255.255.240 network 10.1.1.0 mask 255.255.255.0
Correct Answer: A
QUESTION 15
Which Cisco IOS XR Virtualization technology provides full isolation between virtualized routing instances for extra control plane resources?
A. HVR
B. SVR
C. SDR
D. DRP
Correct Answer: C
QUESTION 16
Refer to the exhibit.
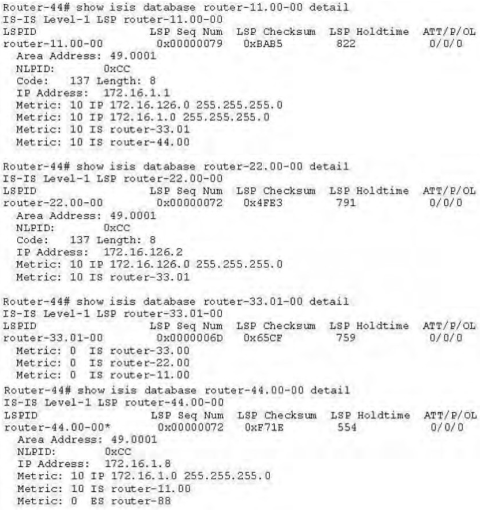
Which router is the DIS?
A. router-22
B. router-44
C. router-33 and router-44
D. router-11
E. router-33
Correct Answer: E
QUESTION 17
Which is one difference between H-VPLS and VPLS? 400-201 dumps
A. VPLS is a point-to-point Layer-2 services and H-VPLS is a multipoint Layer-2 services.
B. H-VPLS reduces signaling overhead and packet replication requirementsfor the provider edge.
C. VPLS improve scalability concerns identified on H-VPLS implementation.
D. H-VPLS connects using also other Layer-2 encapsulation such as PPP and VPLS connects using
Ethernet encapsulation only
Correct Answer: B
QUESTION 18
A network engineer wants to deploy a solution that allows for 200 DS1 s and 100 DS0s that are multiplexed to a single interface on a Cisco 7600 Series Router. Which interface type satisfies this requirement?
A. Channelized T3/E3 (DS0)
B. Channelized OC-12/STM-4
C. OC-12/STM-4
D. OC-48c/STM-16
Correct Answer: A
QUESTION 19
In an MPLS VPN environment, the QoS marking over the MPLS backbone must be different from the one that is received from the customer. The forwarding on the egress PE is based on the marking that is set by the ingress PE. Which null label and QoS mode can achieve this?
A. MPLS explicit null with pipe mode
B. MPLS implicit null with short pipe mode
C. MPLS implicit null with uniform mode
D. MPLS explicit null with uniform mode
E. MPLS explicit null with short pipe mode
F. MPLS implicit null with pipe mode
Correct Answer: A
QUESTION 20
With EIGRP DUAL, a feasible successor is considered loop-free if which condition is true?
A. Its AD is equal to the metric of the successor
B. Its AD is less than the successor's FD
C. Its AD is equal to the successor's FD
D. Its AD is greater than the successor's FD
E. Its FD is equal to the metric of the successor
Correct Answer: B
Newest helpful Cisco CCIE Service Provider 400-201 dumps exam practice files in PDF format free download from leads4pass. The best useful latest Cisco CCIE Service Provider https://www.leads4pass.com/400-201.html dumps pdf training resources which are the best for clearing 400-201 exam test, and to get certified by Cisco CCIE Service Provider, download one of the many PDF readers that are available for free.
High quality Cisco CCIE Service Provider 400-201 dumps vce youtube: https://youtu.be/pwJQ6ekenyo
